What is your Key focus areas? *
AI Workflow and Operations
Data Management and Operations
AI Governance
Analytics and Insights
Observability
Security Operations
Risk and Compliance
Procurement and Supply Chain
Private Cloud AI
Vision AI
Get Started with your requirements and primary focus, that will help us to make your solution

Next-gen Managed Security Services encompassing a holistic approach for Multi Cloud Security, Cyber Security, DDOS protection, Data Protection and ...

Discover essential tools and best practices for security operation center to enhance cybersecurity and streamline incident response.

Cloud Security Pillar, Challenges and its Best Practices to protect data, applications, and infrastructure in a cloud computing environment
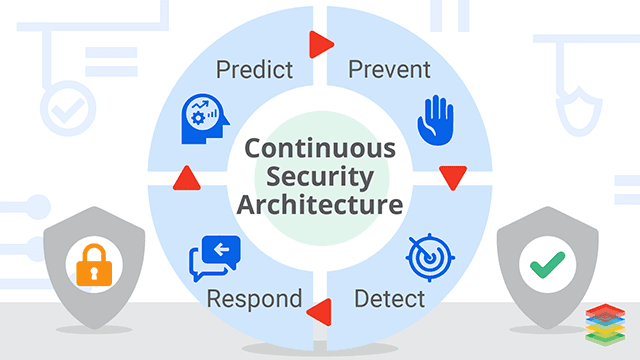
Continuous security automation for DevOps and Microservices ensures proactive security, efficient threat detection, and streamlined compliance ...

Get insights into essential tools and architecture for cloud native security, strengthening your defenses against cloud threats.
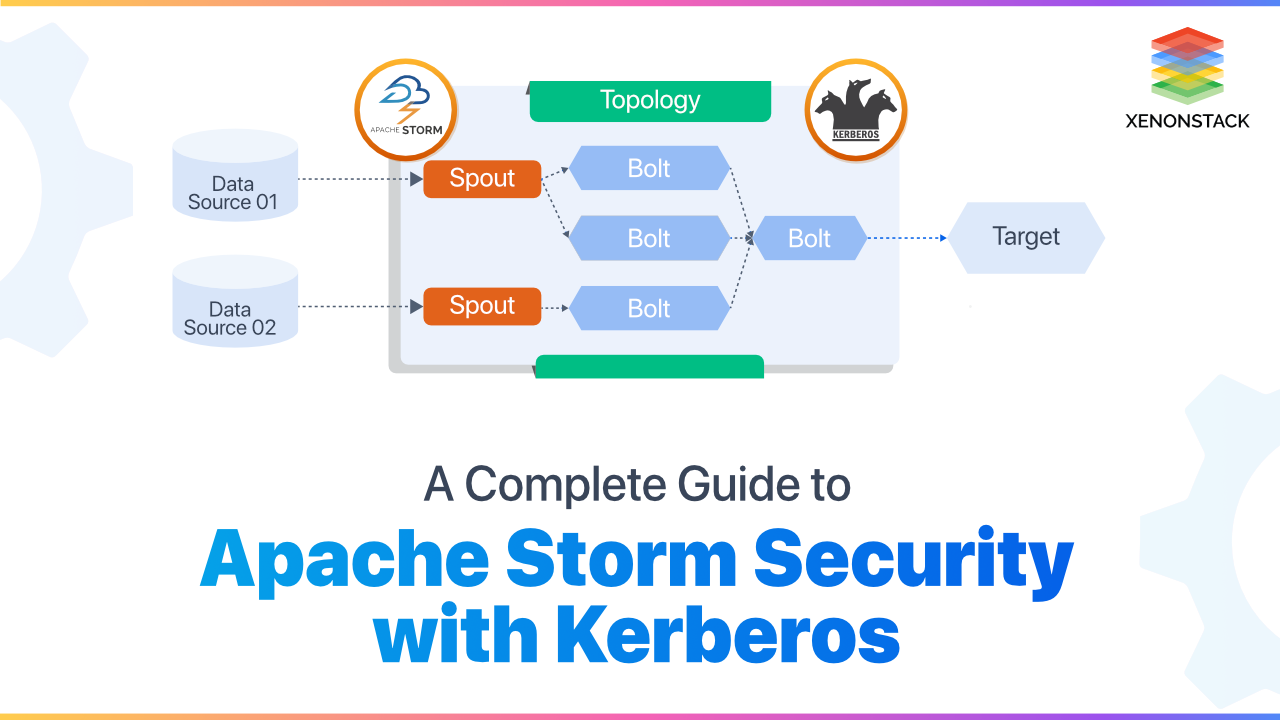
Apache Storm security in conjunction with Apache Kerberos best practices, design, and functionality, enables businesses to process data securely.

AWS Security Tools, Configuration and its use cases to check the configuration of the resources and records valuable information.

Application security Checklist and strategy to consider in 2023 for securing applications against emerging cyber attacks in evolving threat landscape.
Learn how implementing Kafka Security with Kerberos in a Kubernetes Environment enhances data protection and scalable infrastructure.
Supply Chain Security best practices to help enterprises to detect and remediate vulnerabilities throughout the software development lifecycle.

Cybersecurity Framework and best practices for businesses to manage risks and reduce exposure to vulnerabilities that cyber criminals may exploit.

Learn how Strengthening Apache ZooKeeper Security Using Kerberos enhances your cluster’s safety and integrity with robust authentication.

Application security best practices to keep enterprises on top of security for minimizing the risk of data and code breaches.
This guide serves as a comprehensive guide to multi-cloud security, essential for organizations navigating complex cloud landscapes.

Vault Kubernetes is ideal for Secret Management in Kubernetes and offers critical services in the fields of Identity Management, and Compliance.

Digital identity is the key for enabling Web 3.0 to interact securely and provide privacy, control, openness, and interoperability.

Website Security Measures, checklist and Tools, Best Practices for implementation of security in websites from being hacked or any unauthorised ...
Site Reliability Engineering (SRE) bridges gap between development and operations team. Get to know its benefits, principles, and much more.
Ensure robust serverless security with best practices to mitigate risks, prevent breaches, and enhance cloud infrastructure protection.

SecDevOps employs continuous and automated security testing even before the application is deployed, It ingrains culture of a security-first firm ...
Learn what is continuous security testing and its critical role for maintaining secure, resilient software applications.
Cloud Security is a set of policies, procedures, and controls that together protects Cloud-Based Applications, data, and Infrastructure.

Penetration testing vs Ethical hacking. The complete differences to understand the testing strategy and empower the security system wisely.

GDPR Compliance Checklist and requirements for every business to protect personal data and privacy of European Union (EU)

HIPAA Compliance checklist, security rules and Privacy for the protection of patient information with the increase in electronic medical records

Apache HBase Security Architecture and its component to secure HBase with Kerberos and create a protected service session.

Container Security Benifits, framework, Best practices, and solutions to implement Docker and Kubernetes for deploying application operations quickly.

Apache Hadoop security with Kerberos and Ranger ensures robust authentication, authorization, and auditing for big data environments.
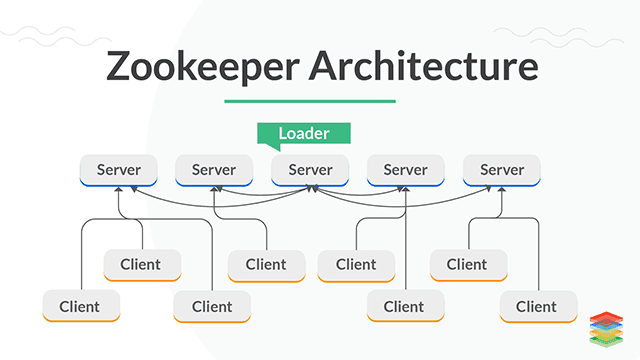
Apache ZooKeeper Security, Architecture, and its Installation on AWS EC2 Instance for managing large hosts, maintenance and configuring information.
Understanding Botnets and how does it work, best Anti-Botnet Tools and Best Practices to protect endpoint devices and malware unbeknownst to users.

Secure Coding Best Practices for producing better quality software products with fewer security bugs and other security-oriented features.

Release Management Process Flow lifecycle, tools and Best Practices to manage the development, testing, deployment, and maintenance of software ...

Agentic Process Automation in Logistics & Supply Chain Management optimizes workflows, improving efficiency and decision-making

Learn effective strategies with The Ultimate Guide to Application Modernization Strategy for successfully upgrading your legacy systems.
Overview of benefits and Implementing DataOps as a Service in Enterprise to bring streamlined changes in data analytics throughout the life cycle
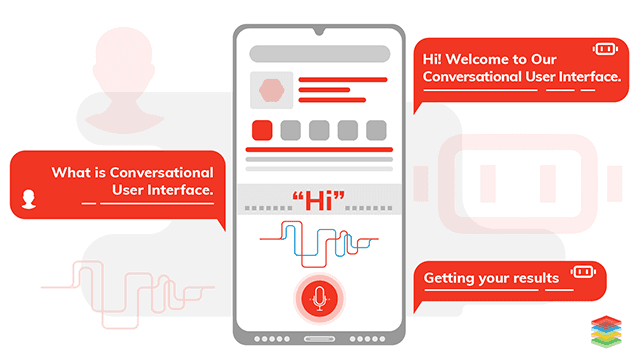
CUI tools, frameworks, and their applications are needed for the best customer experience strategy and design to interact with humans or AI bots.

Real-time intelligence is the process of delivering business intelligence about business operations as they happen in near-to-zero latency.

The transformative impact of ai and emergingtechnologies on the world of finance and banking
6 min | Dr. Jagreet Kaur

Comprehensive approach combines cost forecasting, resource optimization, and financial accountability
4 min | Dr. Jagreet Kaur

Unleashing data agents empowers real-time insights, driving smarter decisions and transforming business operations effectively
5 min | Dr. Jagreet Kaur
AI continuously monitors systems for risks before they escalate. It correlates signals across logs, metrics, and traces. This ensures faster detection, fewer incidents, and stronger reliability
AI converts camera feeds into instant situational awareness. It detects unusual motion and unsafe behavior in real time. Long hours of video become searchable and summarized instantly
Your data stack becomes intelligent and conversational. Agents surface insights, detect anomalies, and explain trends. Move from dashboards to autonomous, always-on analytics
Agents identify recurring failures and performance issues. They trigger workflows that resolve common problems automatically. Your infrastructure evolves into a self-healing environment
AI continuously checks controls and compliance posture. It detects misconfigurations and risks before they escalate. Evidence collection becomes automatic and audit-ready
Financial and procurement workflows become proactive and insight-driven. Agents monitor spend, vendors, and contracts in real time. Approvals and sourcing decisions become faster and smarter