
What is Penetration Testing?
Penetration testing, also known as pen testing, is a procedure used to assess the loopholes and weak points of a given security system. Organizations use this type of testing to recognize various security loopholes and vulnerabilities and finally calculate the security risks. Penetration Testing usually consists of five phases, which are as follows:
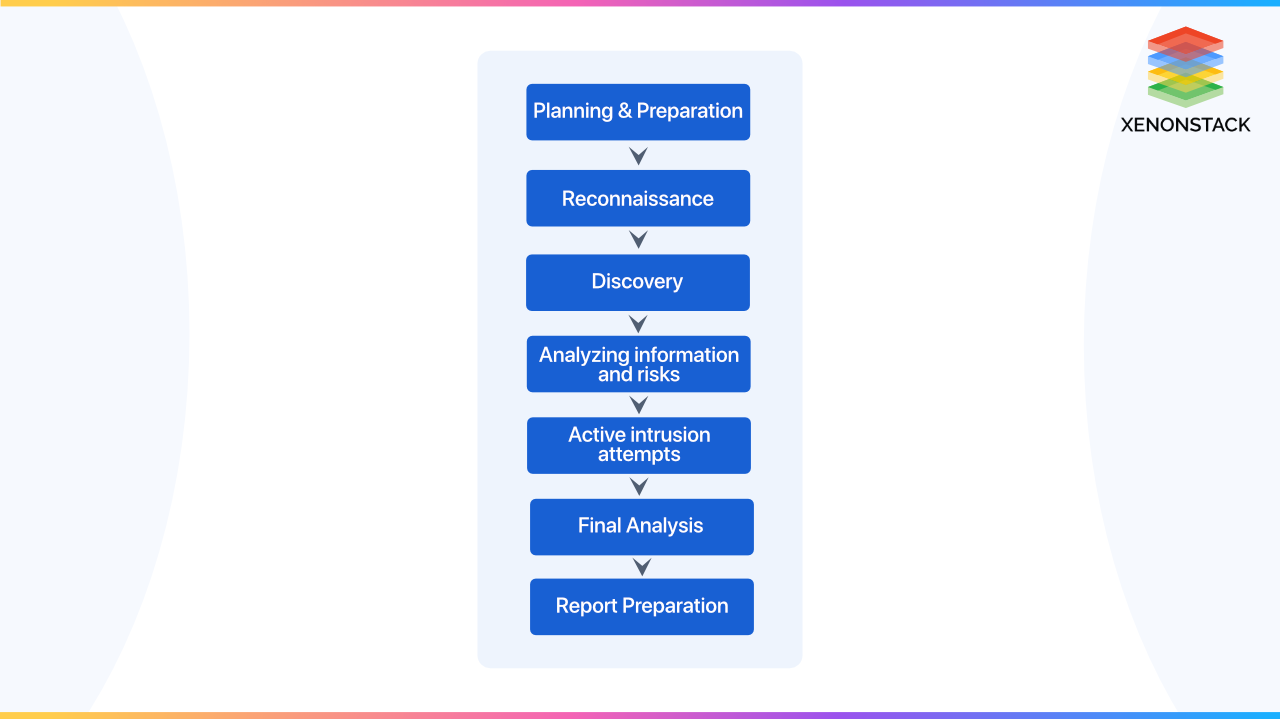
- Planning and Reconnaissance
- Scanning
- Gaining Access
- Persistent Access
- Report Making
A process to identify security vulnerability within an application by evaluating a system or network with the help of different malicious techniques.Click to explore about our, Penetration Testing Tools and its Methods
We can compare it with the real-time activity of checking all possible entry points of our house like the doors, windows, and shafts to ensure that no thief enters the house.
What tools are used for Penetration Testing?
The best Penetration Testing tools are described below:
Metasploit
- Metasploit is the most used Penetration testing framework.
- It helps the security team to verify and manage various security assessments.
- It has an easy-to-use Graphical User Interface.
- Platforms: Mac Os X, Windows, and Linux.
- It is a free tool.
BeEF
- BeEF is an abbreviation for Browser Exploitation Framework
- This tool is best for testing a web browser.
- It helps in connecting multiple browsers.
- It helps in exploring the issues that occur beyond the client system.
Smoke Testing helps a QA team to get confirmation QA team can proceed for further testing or not.Click to explore about our, Smoke Testing Tools and its Best Practices
What are the different types of penetration tests?
The different types of penetration tests:
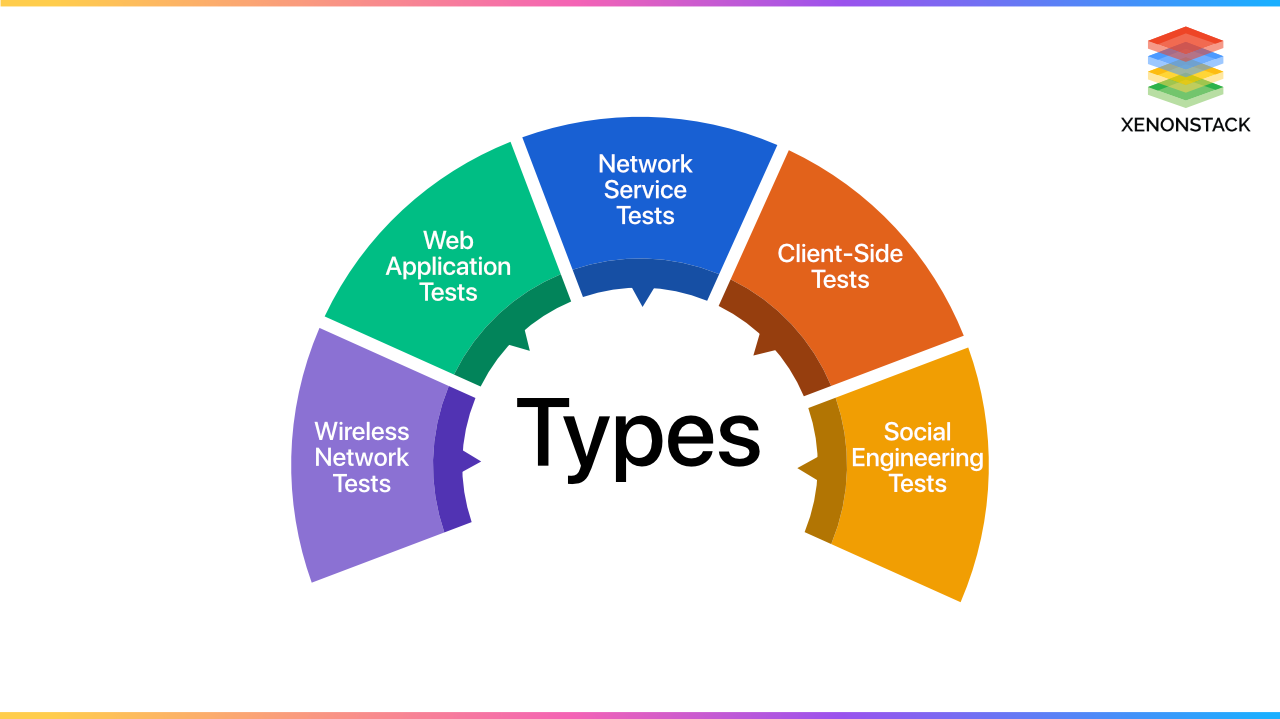
Network Service Tests
Its main aim is to find various vulnerabilities and loopholes in the Client's network infrastructure. As the network can have both internal and external access points, it is compulsory to execute tests locally at the client site and remotely from the outside world.
- In these tests, the pen testers usually target the following network areas,
- Firewall configuration testing.
- Stateful analysis testing.
- Firewall bypass testing.
- IPS deception.
- DNS level attacks which include.
Web Application Tests
- It is one of the most intense and detailed types of testing.
- In this, the following areas are covered,such as web applications, browsers and their parts like ActiveX, Applets, and Scriptlets are covered.
- As this type of testing usually inspects the endpoint of the application in which a customer requires regular interactions, it requires intense planning and time investments.
A type of testing to prove that software application is working as per requirements as mentioned in the specified documents.Click to explore about our, Sanity Testing Techniques and Tools
Client-Side Tests
- The main aim of these types of tests is to assess the security threats that usually occur locally.
- It may include applications like Git clients, Putty, various browsers like Chrome, Firefox, Safari, IE, Opera, and various packages like Adobe Page Maker, Photoshop, and media players.
- In these types of tests, the threats can be homegrown.
Wireless Network Tests
- This test is mainly intended to examine the wireless devices like tablets, laptops, notebooks, iPods, and smartphones deployed on the client site.
- In addition to these devices, the pen tester should also prepare tests for the protocols used to configure the wireless system.
- These tests usually take place at the customer site.
Social Engineering Tests
- These tests usually mimic the attacks that an organization's team member could perform to initiate a breach.
- These tests are further divided into two sub-tests
Remote Tests: In these tests, a tester conducts an attack through a phishing email campaign. It mainly verifies that a team member does not share confidential data via electronic mail.
Physical Tests: In these types of tests, the tester needs to contact the subject directly to redeem sensitive data. It may include activities like Intimidation, Dumpster Diving, etc.
A way of protecting the websites and web application from being hacked or any unauthorized access.Click to explore about our, Website Security Benefits | Tools | Measures
What is Ethical Hacking?
An ethical hacker may be an information security expert whose main aim is to penetrate an application, system, or network to assess or monitor various security flaws or loopholes that an actual hacker can misuse. The role of an ethical hacker demands the same skills as that of an actual hacker. These skills include:
- The dispatching of phishing emails to users.
- Attack on passwords.
- The exploitation of various system configurations.
The role of an Ethical hacker comes into play before the production of a new application or system.
The various types of Ethical hacking are:
- Web application hacking
- Social engineering
- System hacking
- Hacking wireless networks
- Web server hacking

Which tool is used for Ethical Hacking?
The mostly used tools for ethical hacking are listed below:
Acunetix
- Acunetix is an automated ethical hacking tool.
- Platform: Windows, Mac, RedHat 8, etc. & Web-based.
- It is used for End-to-end web security scanning.
- It is not an open-source tool.
Netsparker
- Platform : Windows & Web-based
- Netsparker is used for Accurate and automated application security testing.
- It is one of the most accurate ethical hacking tools that mimic a hacker's moves to identify anomalies like SQL Injection and Cross-site Scripting in web applications and APIs.
Ethical Hacking vs. Penetration Testing
| Ethical Hacking | Penetration Testing | |
| Scope | It usually has a broader scope in comparison to penetration testing. It monitors the entire environment for a longer period of time. | It is performed on a particular aspect and not on the entire environment based on the given budget and time constraint. |
| Permission Required | In this, the ethical hacker requires the permission of the whole system. | In this, the tester requires the permissions of only the specific areas which they are testing. |
| Who conducts? | Ethical hacking is conducted by individuals who must have extensive knowledge of programming as well as other hacking techniques. | Penetration testing is conducted by the individual who has expertise and knowledge in this particular type of testing. |
| Reporting | Ethical hackers must have good experience in generating in-depth reports along with suitable solutions. | Penetration testers are responsible for generating detailed reports for the test performed. |
| Certification | It is compulsory for an ethical hacker to be certified. | It is not compulsory for a penetration tester to be certified if they hold an ample amount of experience. |
Conclusion
A certified tester makes various plans for performing penetration testing by imitating real-life scenarios. This process is usually carried out by taking all the necessary permissions from the required authorities and concerned people and businesses so that it does not cause any harm to anyone.
- Know more about DevSecOps Tools and Continuous Security
- Are your applications on the cloud? Explore our Cloud Security for Hybrid and Multi-Cloud
.webp?width=1921&height=622&name=usecase-banner%20(1).webp)


