
Introduction to Penetration Testing
It's referred to as a Pen test. Penetration Testing is used to evaluate the security of an IT infrastructure. It is a process to identify security vulnerability within an application by evaluating a system or network with the help of different malicious techniques. Vulnerable areas of system or application identified through a process of an authorized simulated attack on the system. The primary purpose of executing this type of testing on a system is to track the data from outsiders like hackers that make unauthorized access to a system.
Smoke Testing helps a QA team to get confirmation QA team can proceed for further testing or not. Click to explore about, Smoke Testing Best Practices
Once a vulnerability identified in a system, then that weak area of the system used by the hacker to gain access to a system or to get sensitive information from a system. The one who executes penetration testing on a system, but in the legal way referred to as an ethical hacker. These types of hackers hired by an organization to find out vulnerable areas of an application, later on, these vulnerable areas cannot find out by the unauthorized hackers to damage or destroy a system.
Why Penetration Testing Matters?
WannaCry ransomware is an attack that spread in May 2017. It had locked more than 2 lakh computers around the whole world and demanded payments in the form of a Bitcoin Cryptocurrency. It was an attack that has affected many big organizations around the globe. With more and more Cyber attacks happening these days, it's becoming unavoidable to avoid a penetration testing attack As WannaCry ransomware attack affected many computers in May 2017. With an increase in numbers of massive and dangerous attacks, it becomes unavoidable to do Penetration Testing. It is required to execute penetration testing for the security of the system against security breaches or different security parameters depending upon the requirement.
-
Data relative to finance and also critical data transferred securely, it transfers data between different systems and different networks.
-
Nowadays, many clients ask for Penetration testing as part of a software release cycle because of the security of data.
-
It also helps to discover the loopholes of the system.
-
It is important to get aware of business risks if an attack has to happen.
-
Implementing an effective security strategy in an organization is important.
Penetration testing tools help assess the system's security and find the system's vulnerabilities before an attacker. Click to explore about, Top Penetration Testing Tools and Methodologies
Why is Penetration Testing Important?
It has been witnessed a few years back that a majority of organizations are experiencing cyber-attacks ranging from almost twice a year to once every few seconds. Some of these cyber-attacks are targeted, while most of them are random. A targeted cyber-attack signifies that the attacker often referred to as a hacker, knows its security posture and the underlying functionalities. Therefore, it's easier to carry out a targeted attack. A random cyber-attack signifies that the attacker is trying to gain information about the organization's security posture. By carrying out random attacks, he tries to understand the underlying functionalities to carry out a targeted-attack at a later stage. The cyber-attacks also differ in magnitude, impact, method or technique of attack, and risks.
Even the most prepared organizations around the globe cannot deny the chance of the existence of being targeted through a cyber-attack. As businesses and organizations are shifting to cloud environments and growing, their companies are heavily relying upon the internet, and they are preparing themselves to face even more cyber-attacks in the coming years.
With the above scenario, the organizations must prepare 24/7/365 to handle and stop any cyber-attack. Penetration Testing plays a significant role in this scenario. It is always considered a good security practice.
A type of testing to prove that software application is working as per requirements as mentioned in the specified documents. Click to explore about, Sanity Testing Techniques
Penetration Testing is essential due to the following reasons:
-
It is necessary to meet various compliance requirements such as PCI DSS, ISO 27001, HIPAA, GDPR, etc.
-
Help the organizations to decide the potential areas of security that require immediate attention and investment.
-
Simulates real-world attacks. It helps the organization to understand an attacker's perspective and prepare themselves accordingly.
-
Penetration testing allows having an advanced and comprehensive opinion.
-
Helps determine the feasibility of a specific set of attack vectors on the attack surface.
-
Identify high-risk vulnerabilities and a combination of several low-risk vulnerabilities that can be considered high-risk vulnerabilities when exploited in a particular sequence.
-
It helps assess and test the defenses and check whether applied controls are sufficient to detect and respond to cyber-attacks.
What are the benefits of Penetration Testing?
Penetration testing is beneficial in many ways and one of those is that it helps to find the vulnerable areas of an application in advance by using an authorized hacker, in order to avoid the risk of getting attacked by an unethical hacker. The benefits of using Penetration Testing are as follows:
-
Safeguard the confidentiality, integrity, and availability of any computer resource.
-
Verify and examine the security configuration of the devices.
-
Helps the organization to recognize and respond to various types of cyber-attacks.
-
Test new implementations.
-
Provides a complete overview of the security posture of the organization.
-
Categorize vulnerabilities in terms of magnitude and their impact on the business.
-
Understand and mitigate the risks before being exploited by an attacker.
-
Protect the organization's reputation and gain a customer's trust.
-
Prevent data breaches.
-
Test the organization's defense capabilities.
-
Ensure business continuity.
-
Reveal unnoticed vulnerabilities and possible real-attack scenarios.
Website Security is a way of protecting the websites and web application from being hacked or any unauthorized access. Click to explore about, Website Security Benefits
How does Penetration Testing Work?
There are different types of Penetration tests -Social Engineering Test
It is a type of testing, executed to make a person reveal sensitive information such as a password or it can be business-critical data, etc. These types of tests made with the help of a phone or the Internet to target specific help desks, employees, and processes. In this human errors are the primary causes of security vulnerability. These security standards and policies followed by all the staff members to avoid any penetration attack. For example - Sensitive information should not be shared in email or phone communication. Security audits conducted to identify incorrect flaws.
Web Application Test
It is a type of testing to check the vulnerability of web applications and software programs positioned in a specific environment.
Physical Penetration Test
-
It is a strong security method.
-
Penetration Test is used to protect sensitive data.
-
It is normally used in military and government facilities.
-
In such types of organizations network devices and access points tested for possibilities of security flaws.
-
It is not relative to software testing.
Network Service Test
-
It is a type of testing through which loopholes and the opening of the network identifier.
-
It's all about identifying an entry point for a system or application and also to check what kind of vulnerabilities be there.
-
It is done locally or remotely.
Client-Side Test
This type of testing is all about searching and find out a vulnerability in client-side software systems.
Remote Dial-Up war Dial
It finds out modems in an environment and to login systems connected to this modem by using a technique of a Password Guessing and Brute Forcing.
Wireless Security Test
It is a type of testing that finds out open, unauthorized and less secured hotspot or Wi-fi networks along with this also makes the connection with these unsecured networks such as hotspot or wifi to make testing for the application. As penetration testing categorizes into seven types that are also mentioned above, these above seven mentioned techniques can also be summarized into three, which are explained as following three -
-
Black Box Penetration Testing - It is a type of testing approach, tester accesses a target system, network, and processes without having any internal knowledge of a system. It has an internal level of details such as URL or company name to penetrate a target environment. No code examined for this type of testing.
-
White Box Penetration Testing - To do this type of testing, complete details about a target environment needed such as systems, network, OS, Addresses, source code, schema, etc. It examines code as well as finds out the design and development of relative issues. This type of testing is a simulation of an internal security attack.
-
Gray Box Penetration Testing - It is a type of testing with limited details about the environment. It’s rendered as an external security attack.

What are the Penetration Testing Methods?
There are five types of penetration testing methods that are explained -
External Testing
External penetration tests target assets of application that are visible on an Internet such as a web application itself, company website, email address, and Domain name servers(DNS). The main goal of this type of application is to gain access and extract valuable data from an application on which testing is going to happen.
Internal Testing
In this type of Internet test, a tester with access to an application behind its firewall. Conman's basic scenario covered under this such as an employee whose basic credentials stolen due to a Phishing attack. The phishing attack is a type of attack to steal user's information such as credentials etc.
Blind Testing
It is a type of testing in which the tester is provided only with the name of the organization at which testing performed. Blind Testing is a type of testing that provides a real look at testing. It provides a view of what will occur when actual testing takes place. This gives security personnel a Real-Time observation that how applications executed in Real-Time.
Double-Blind Testing
It is a type of testing, in which a security person does not have knowledge for a simulated attack that is going to occur. It helps to provide a Real-Time view and shows what will happen if an attack going to happen in Real-Time situations.
Targeted Testing
It is a type of testing in which hackers and personal security work together. It provides a security team with Real-Time feedback from an authorized hacker's point of view
What are the five steps of implementing Penetration Testing in Cyber Security?
the five Simple Steps of Penetration Testing are listed below:
Establish Fundamental Rules
It is the first phase of Penetration Testing. The first aim here is to define the scope and goal of the test. It also includes systems to be addressed and testing methods to be used to test that system.
-
Define the expectations and connect information between the testing team and the client.
-
Identify all the involved teams involved and if they are aware of the evidence.
-
Set the start dates along with non-working periods.
-
Obtain formal approval, including scope, signatures, and legal requirements aka “Statement of Work” (SoW).
Passive and Active Scanning
Understand how a target application responds to the different types of intrusion attempts. It can be done typically by the following ways. For this, there is a need to go through following two types of analysis -
Passive Scanning requires all the information while maintaining zero contact among the test equipment and target. Passive scanning, sometimes also known as Open Source Intelligence (OSINT). It includes:
-
Online databases
-
Search the trash
-
Social networking sites
-
Search Engines
Active Scanning is the public exposure of the target with scanning products, including: Commercial Scanning
- Network mapping
- Sniffing network traffic
- Wireless scanning
- DNS zone transfers
Obtain the Footprints
Testers then try and exploit these vulnerabilities, typically by escalating privileges, stealing data, intercepting traffic, etc., to understand the damage they can cause. It is a stage that uses web application attacks such as cross-site scripting, SQL injection, and backdoors to uncover the target system's vulnerabilities. Testers then try to exploit vulnerabilities through breaking privileges issue, stealing data and intercepting traffic, etc. This helps to understand what type of damage will occur if the attack will occur in actuality. Conduct complete testing of the target systems to identity:
-
Open ports information
-
Running services
-
User account
-
Operating System patch level and type
-
Applications and their patch level
-
Select the Target System
Exploit Discovered Vulnerabilities
The main aim of this stage is to check that if a vulnerability used to achieve a persistent presence in an exploited system. This type of attack access for a large time in an exploited system to steal important information from a system. Run appropriate attacks against suspicious exposures.
Analysis and Reporting
The penetration test results will be compiled into a report, which will include:-
All the exploited vulnerabilities
-
Accessed sensitive data
-
Time duration spend by the pen tester in the system undetected
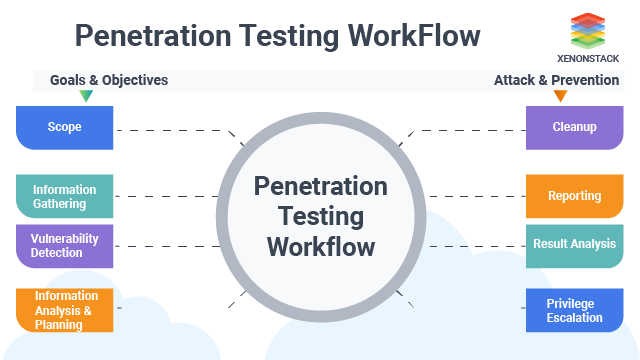
What are the Types of Penetration Testing?
There are three ways or techniques to do penetration testing. These are mentioned as following --
The manual way of penetration testing.
-
An automated way of penetration testing.
-
Combination of Manual and Automation of Penetration Testing.
What are the best practices of Penetration Testing?
- To do Penetration Testing, it is required that the system should be deployed.
- Perform testing on Real-Time.
- Check the behavior of the application by applying attacks on the application in Real-Time.
System Testing enables to test, validate and verify both the Application Architecture and Business requirements. Click to explore about, System Testing Techniques
In conclusion, Penetration Testing executed when the application is working properly. Then a different type of testing method applied to the application, depending upon the requirement of the application. It finds vulnerable areas of application in advance by an authorized hacker so that, it cannot be hacked by any unethical hacker.
Next Steps towards Penetration Testing
Talk to our experts about taking the next step toward penetration testing. Learn how industries and organizations leverage advanced security assessments, automated vulnerability detection, and risk mitigation strategies to strengthen their cyber defenses. Discover how penetration testing helps identify security gaps, prevent cyber threats, and ensure compliance with industry standards. Enhance your IT security and optimize threat response with AI-driven penetration testing solutions today!
.webp?width=1921&height=622&name=usecase-banner%20(1).webp)


