
Getting Started with DevOps
DevOps was born to help developers and operations teams work better. It has been accepted as a standard practice. However, with the rise in zero-day exploits and the need to quickly restore services and make them secure by design, it only makes sense to factor security into DevOps. Thus, Security Testing in DevOps is not only important but essential. If security is not taken care of, delays in the software delivery can affect brand and customer loyalty.
Key Points Being Discussed:
-
Security Testing in DevOps: Essential to integrate security practices early in the development lifecycle.
-
Zero-Day Exploits: Highlight the increased urgency of identifying and mitigating vulnerabilities before they can be exploited.
-
Quick Restoration of Services: Services must be swiftly recovered from attacks or failures while ensuring security is baked into the process.
-
Secure by Design: Ensuring that security is part of the design and development stages rather than bolted on afterward.
-
Impact of Delays: Delays in delivery due to security issues can harm customer trust, brand reputation, and business continuity.
-
DevSecOps: A shift towards a collaborative approach to DevOps, incorporating security at every stage of the software development lifecycle.
What You Need to Know About Security Testing?
Security testing is a type of software testing that ensures that any application or system is free from threats, vulnerabilities, and risks. This testing is about finding all possible weaknesses in the system, which might result in a loss of an organization's data or information. It helps detect all possible security risks in the system and assists developers in fixing these problems through coding.
A process in which, Modern software engineering Culture and Practices to develop software where the development and operation teams work hand in hand as one unit. Click to explore about, What is DevOps and it's Processes
The Necessity of Security Testing in DevOps
-
Security testing is essential to safeguard data records that are lost and stolen by other industries.
-
To avoid loss of customers' trust.
-
For securing web applications from unauthorized hackers.
-
Security testing helps improve the current system and ensures that the system will work for a longer time.
-
To avoid website downtime and time loss and reduce the cost of recovering from the damage.
-
Security tests help in finding loopholes that can cause the loss of valuable information.
Fundamental Principles of Security Testing
The basic principles of security testing in DevOps are listed below:
Confidentiality
This is equivalent to security, and it has a set of rules that limit access to any information. It protects against disclosure of information to an unauthorized person and ensures that only the delegated person gets access to the data.
Integrity
Integrity is like the consistency and accuracy of data over its entire life cycle. It allows the transfer of accurate and desired data without any modification from senders to intended receivers and ensures that unauthorized people cannot modify data.
Availability
In availability, all data, hardware, and software need to be maintained, and hardware and software repairs must be performed immediately when required. It is essential to ensure that the information concerned is readily accessible to the authorized viewer at all times.
The approach of taking the action of testing the software and moving it to the left in the delivery pipeline. Click to explore about, Shift Left Testing Benefits and Approach
Common Challenges in Implementing DevSecOps Approaches
-
Cultural Resistance: Employees may hesitate to adopt DevSecOps due to a lack of understanding of its principles or fear of change. This can create friction between development, security, and operations teams, delaying the integration of security testing practices.
-
Skill Gaps: Many teams lack the necessary knowledge in cyber security and security testing techniques, making it difficult to implement proper security measures. Upskilling staff or hiring experts in cyber security penetration testing can be both time-consuming and costly.
-
Tool Overload: With numerous security testing tools available, teams may struggle to choose the right ones. Managing too many tools, such as vulnerability scanners and DevOps security tools, can lead to inefficiencies and potential gaps in security coverage.
-
Integration Complexity: Integrating security testing tools into existing CI/CD pipelines can be challenging. Compatibility issues between DevOps tools and security testing services may cause delays and increase the risk of overlooking vulnerabilities.
-
Resource Allocation: Implementing DevSecOps requires significant resources, both budgetary and personnel. Organizations may face difficulties reallocating resources from other areas to prioritize security best practices and cyber security testing initiatives.
Top Security Testing Tools Available
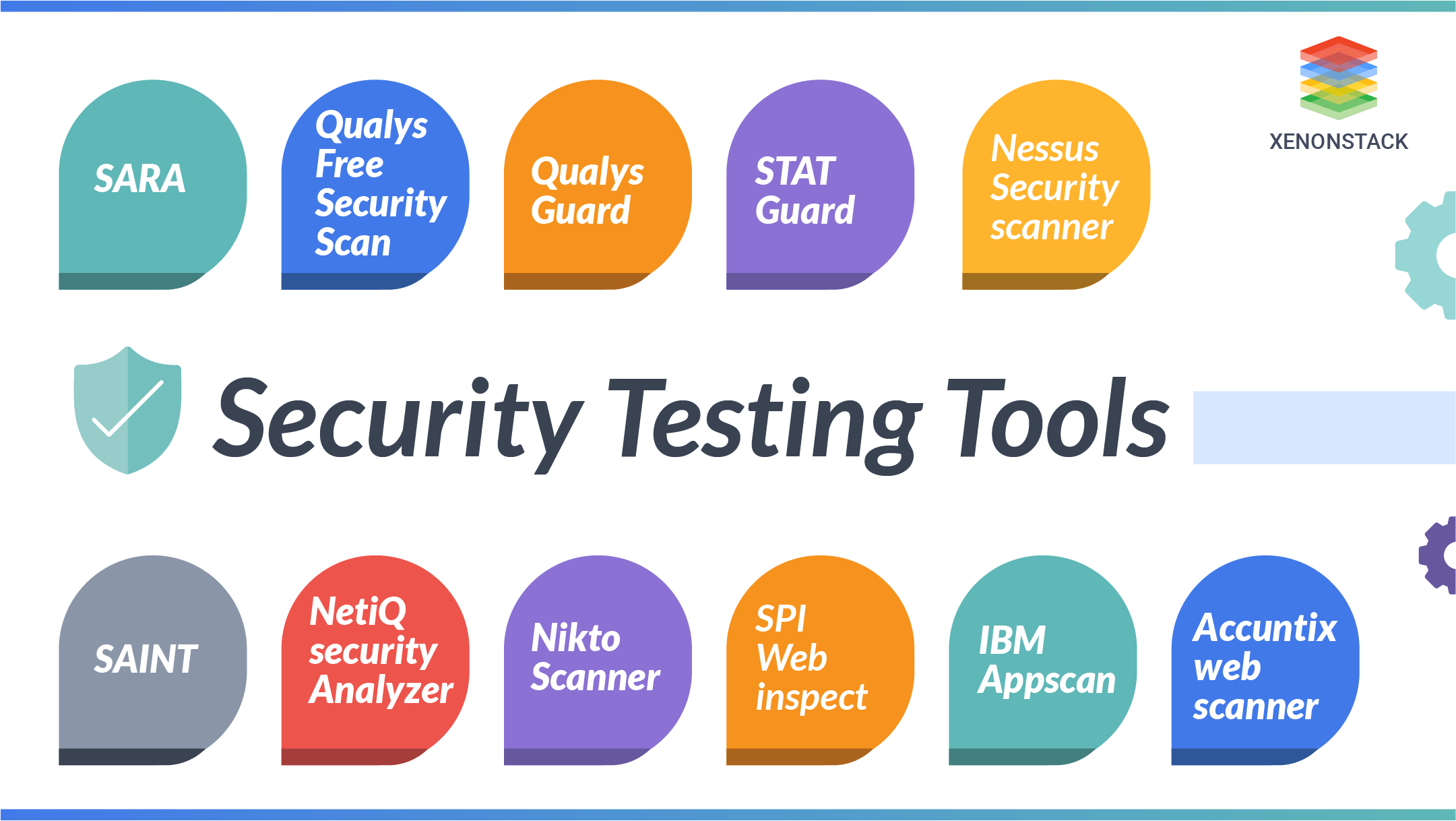
Fig 1: Security Testing Tools
Here are the best security testing tools:
-
XenonStack’s Cloud Security & Compliance Platform: A comprehensive solution for continuous cyber security testing, vulnerability management, and compliance monitoring to strengthen DevSecOps posture.
-
SARA: A security testing tool that identifies vulnerabilities in web applications and systems, helping assess cyber security risks through static and dynamic analysis.
-
Qualys Free Security Scan: A free tool for performing cyber security testing to discover vulnerabilities and weaknesses in web applications and networks.
-
Qualys Cloud Platform: A cloud-based platform that provides continuous security testing and vulnerability management and is integrated with DevOps tools for real-time security monitoring.
-
STAT Guard: A real-time security testing tool for vulnerability detection and patching designed to mitigate cyber security risks.
-
Nessus Security Scanner: A widely-used security testing tool for vulnerability scanning, helping identify security flaws like missing patches and misconfigurations.
-
SAINT: A network vulnerability scanner that performs penetration testing and detects cyber security risks in applications and systems.
-
NetIQ Security Manager: A security testing tool offering continuous monitoring and vulnerability assessments to improve cyber security posture.
-
Nikto Scanner: An open-source web security testing tool for detecting vulnerabilities like SQL injection and XSS in web applications.
-
SPI WebInspect: A dynamic web security testing tool for identifying critical web application vulnerabilities, including XSS and injection flaws.
-
IBM Appscan: A comprehensive security testing solution for detecting vulnerabilities in web applications, improving cyber security during development.
-
Acunetix Web Scanner: An automated web security testing tool that scans for common vulnerabilities like SQL injection and XSS in web applications.
Categories of Security Testing in DevOps
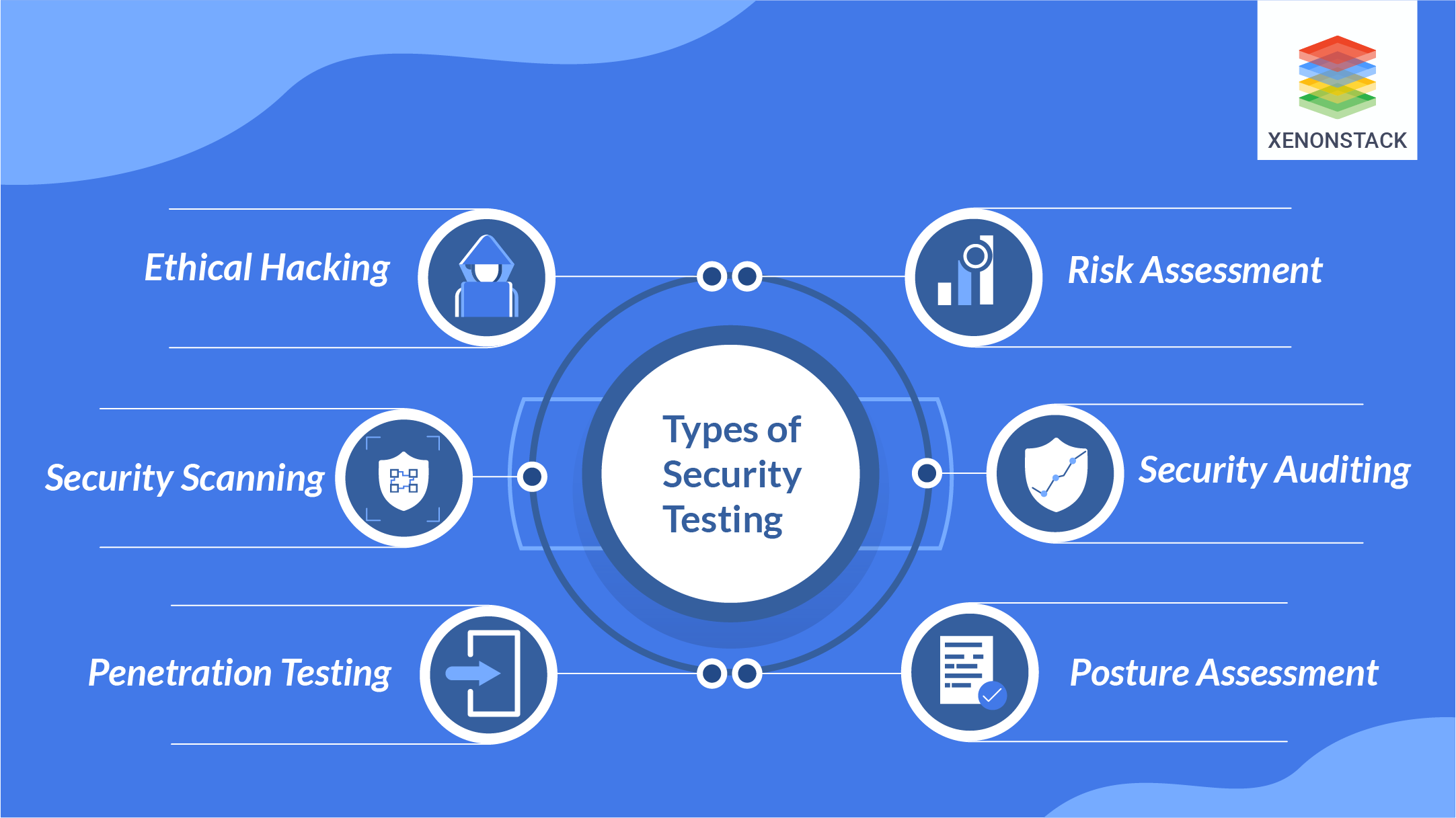
Fig 2: Categories of Security Testing in DevOps
-
Vulnerability Scanning: In this process, the system is scanned to identify vulnerable signatures, verifying access control with the operating system and technology stack to uncover potential cyber security risks.
-
Penetration Testing: This simulates a hacker attack to assess a system's security, targeting visible company assets like websites and email access to uncover weaknesses in the web security testing policies.
-
Ethical Hacking: In ethical hacking, the system is tested from within to expose security flaws in application software. This plays a crucial role in continuous security testing and a mature application security program.
-
Risk Assessment: This involves evaluating the security posture of the system under test, classifying risks as high, medium, or low, and helping prioritize security testing efforts based on cyber security threats.
-
Security Scanning: A thorough analysis of the system is conducted to find weaknesses in the network, identifying vulnerabilities that could lead to data breaches or system exploitation through security scanning.
-
Security Review: The security review process identifies potential security-related issues by examining all components and configurations, ensuring that security best practices are followed to mitigate risks.
Test automation is the utilization of specialized software to control the execution of tests and the comparison of actual outcomes with predicted results. Click to explore about, Test Automation in DevOps
Advanced Techniques for Security Testing
SQL Injection
SQL Injection occurs when an attacker manipulates an SQL query to access or alter data in a database. The web application sends an SQL query to the database, and if the query is not properly sanitized, attackers can inject malicious code to retrieve, modify, or delete sensitive data. SQL injection is a type of code injection used to execute harmful SQL statements.
Cross-site scripting (XSS)
Cross-site scripting refers to a client-side code injection attack wherein an attacker can execute a malicious script (also commonly referred to as a malicious payload) into a legitimate website or web application. It is mainly divided into three types:-
-
Reflected XSS: The malicious script is reflected off the server immediately without being stored.
-
Stored XSS: The script is stored on the server and served to users later.
-
DOM-based XSS: The script is executed by manipulating the Document Object Model (DOM) in the user's browser.
Cross-site Request for forgery
CSRF is a malicious website that requests a legitimate website on which the user is authenticated. The malicious website triggers the request on behalf of the user. The browser automatically sends cookies and session IDs.
Example of Security Testing
-
Strong Password Policy: Ensure passwords follow complexity rules.
-
Encrypted Password Storage: Store passwords in a secure, encrypted format.
-
Login/Logout Functionality: Test login/logout processes to avoid session hijacking.
-
Browser Back Button: Prevent access to sensitive data after logging out of financial apps.
-
Encrypted Data Flow: Ensure sensitive data like credit card details is transmitted securely.

Integrating Security and DevOps with Xenonstack
Xenonstack empowers organizations with automated application security solutions that protect the software driving enterprise operations. By offering a unified platform, Xenonstack ensures seamless integration of security testing throughout the software development lifecycle—from planning and design to production.
By implementing DevSecOps, which integrates security best practices into the CI/CD pipeline, and leveraging threat intelligence, Xenonstack helps businesses proactively identify and mitigate vulnerabilities. This approach ensures that security is built into applications from the start, not tacked on later. As a result, organizations can innovate with confidence, building, buying, and assembling applications while ensuring security and compliance every step of the way.
Areas of Security Testing implementations
Network security: Looking for vulnerabilities in the network infrastructure.
System software security: Testing weaknesses in the various software (operating system, database system, etc.)
Client-side application security: This will check that the client-side browser cannot be manipulated.
Server-side application security: This involves making sure that the server code is free from all possible intrusions.
Benefits of Implementing DevSecOps Techniques and Tools
-
Enhanced Security Posture: By integrating security practices throughout the development lifecycle, organizations can significantly improve their overall security posture and reduce the likelihood of breaches.
-
Faster Time to Market: By detecting and remediating vulnerabilities early, teams can streamline their workflows, leading to faster releases without compromising on security.
-
Cost Savings: Identifying and fixing vulnerabilities early in the development process is typically less expensive than addressing them after deployment, resulting in significant cost savings over time.
-
Improved Collaboration: DevSecOps fosters a culture of collaboration among development, security, and operations teams. This collaborative approach enhances communication and teamwork, leading to better outcomes.
-
Regulatory Compliance Assurance: By embedding compliance checks into the development process, organizations can ensure that their software meets necessary legal and industry standards more consistently and efficiently, reducing the risk of non-compliance penalties.
Final Analysis of Security Testing Best Practices
With cyber threats becoming increasingly sophisticated, continuous security is essential to protecting organizational assets and ensuring business continuity. Security testing techniques like vulnerability scanning and risk assessment are crucial for identifying potential weaknesses in systems before they can be exploited. Regular security reviews and penetration testing give businesses the tools to strengthen their defenses. A solid cyber security strategy boosts market confidence, enhances brand reputation, and ensures compliance with industry standards. In the end, investing in continuous security testing isn't just about preventing breaches—it's about fostering long-term customer trust and loyalty.
- Discover more about SRE Approach to Achieve DevOps
- Explore here the Role of Agile in DevOps
- Learn more about Mastering Security Testing Tools and Best Practices
Next Steps in Deployment of Security Testing for DevOps
Connect with our experts to learn how to integrate security testing into your DevOps pipeline. Explore how industries use DevSecOps tools to enhance security, automate vulnerability scanning, and improve penetration testing. Our solutions help streamline security testing throughout the development lifecycle, boosting efficiency and protecting your applications from threats. Let us help you implement robust security practices for safer, more efficient operations.
.webp?width=1921&height=622&name=usecase-banner%20(1).webp)


