What is your Key focus areas? *
AI Workflow and Operations
Data Management and Operations
AI Governance
Analytics and Insights
Observability
Security Operations
Risk and Compliance
Procurement and Supply Chain
Private Cloud AI
Vision AI
Get Started with your requirements and primary focus, that will help us to make your solution
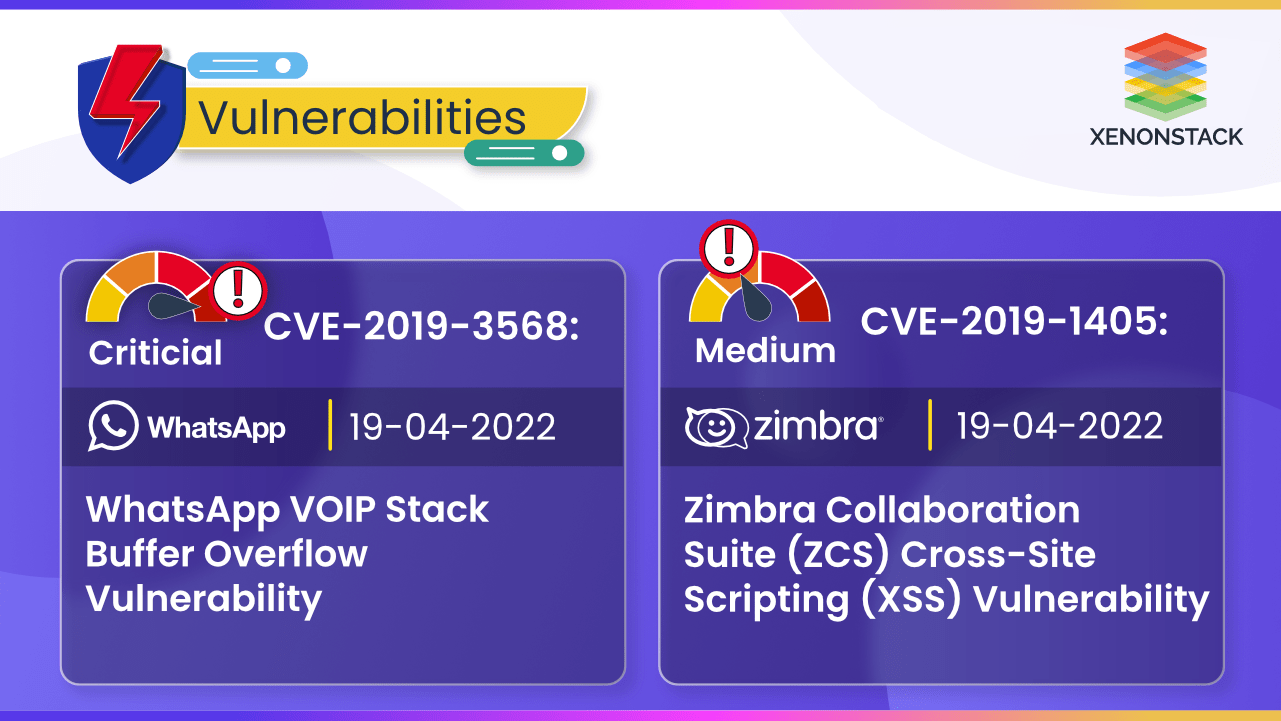
CVE-2019-3568 (Whatsapp) and CVE-2018-6882 (Zimbra) Vulnerabilities allow attackers to remotely inject arbitrary HTML or remotely execute code
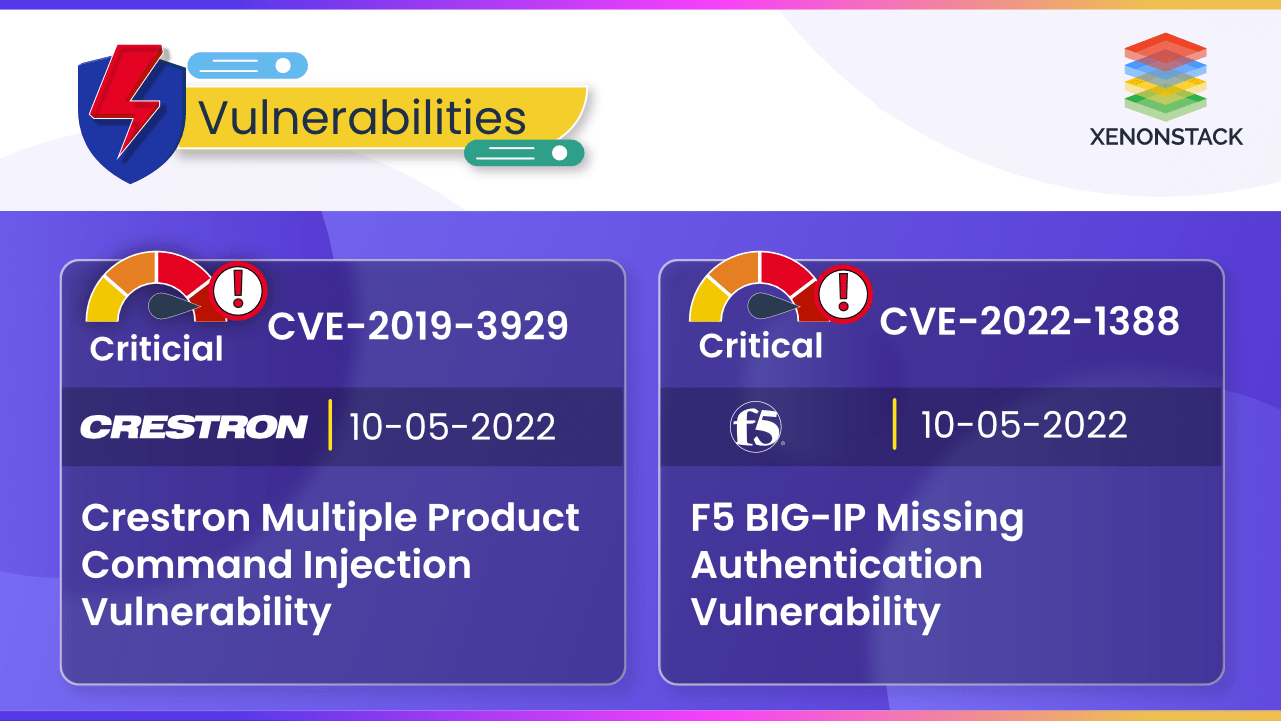
CVE-2019-3929 and F5 CVE-2022-1388 vulnerabilities can leads to priveledges escalation and remote code execution
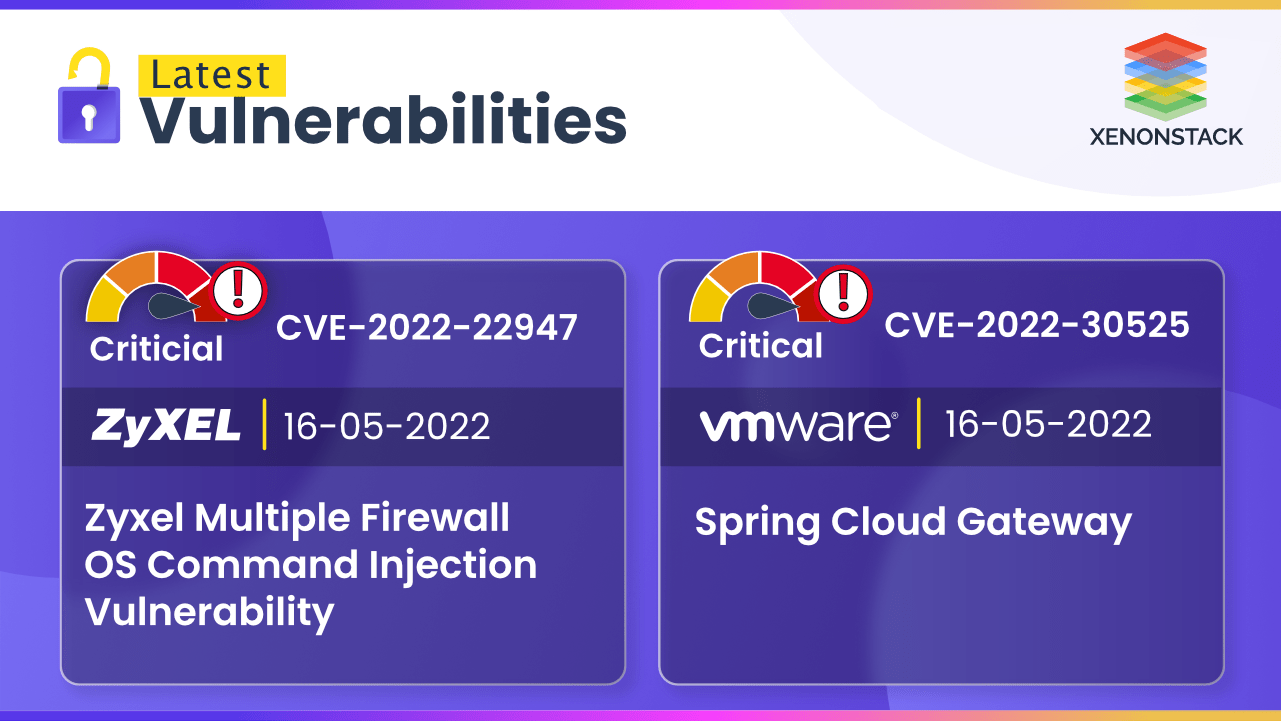
CVE-2022-22947 and CVE-2022-30525 are Code and Command Injection Vulnerabilities that can allow an attacker to modify files and execute OS commands.
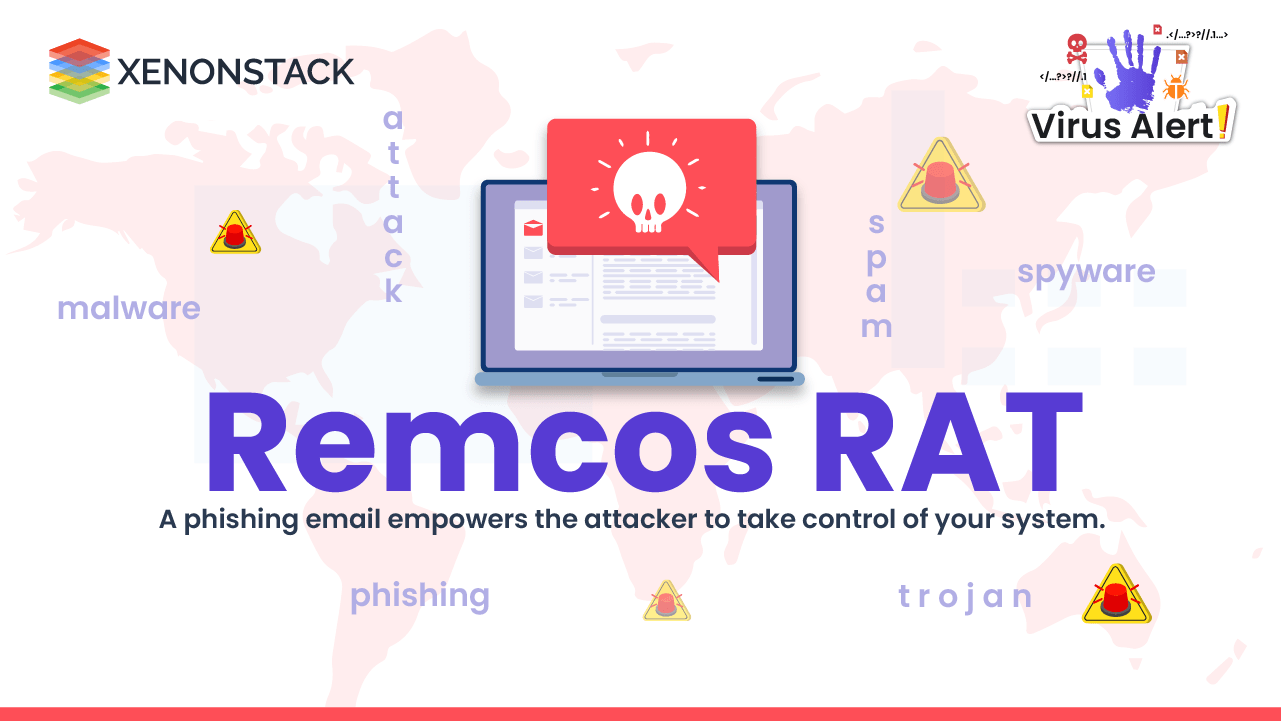
Remcos RAT malware targeting Windows-based computers gives the attacker complete remote control over the systems via phishing email to steal user ...
CodeRed Worm propagates through networks, uses a vulnerability in Microsoft's IIS, and launches a DoS attack to suspend all activities.
The Sasser virus finds a vulnerable system, copies itself into the Windows system directory, and is launched the next time the computer is booted.

Spring4shell (CVE-2022-22965) is a vulnerability in the Spring Java framework that execute code remotely and compromises a huge number of servers

Clop Virus belongs to the Cryptomix ransomware family which actively avoids unprotected systems and encrypts saved files by planting the Clop ...

Tinba is a tiny banker trojan that uses a spoofed website of a financial institution to redirect sensitive information, login credentials to the ...
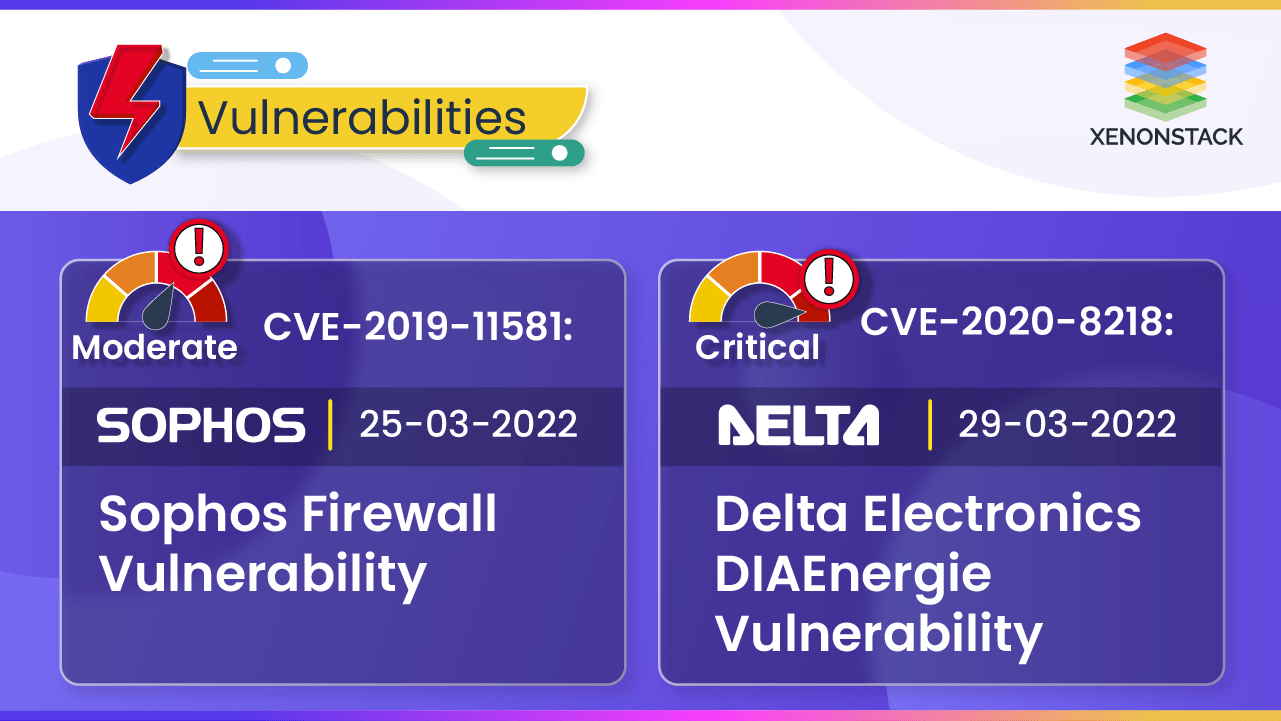
Delta Electronics DIAEnergie (CVE-2022-25880) and Sophos Firewall (CVE-2022-1040) Vulnerabilities allows remote code execution
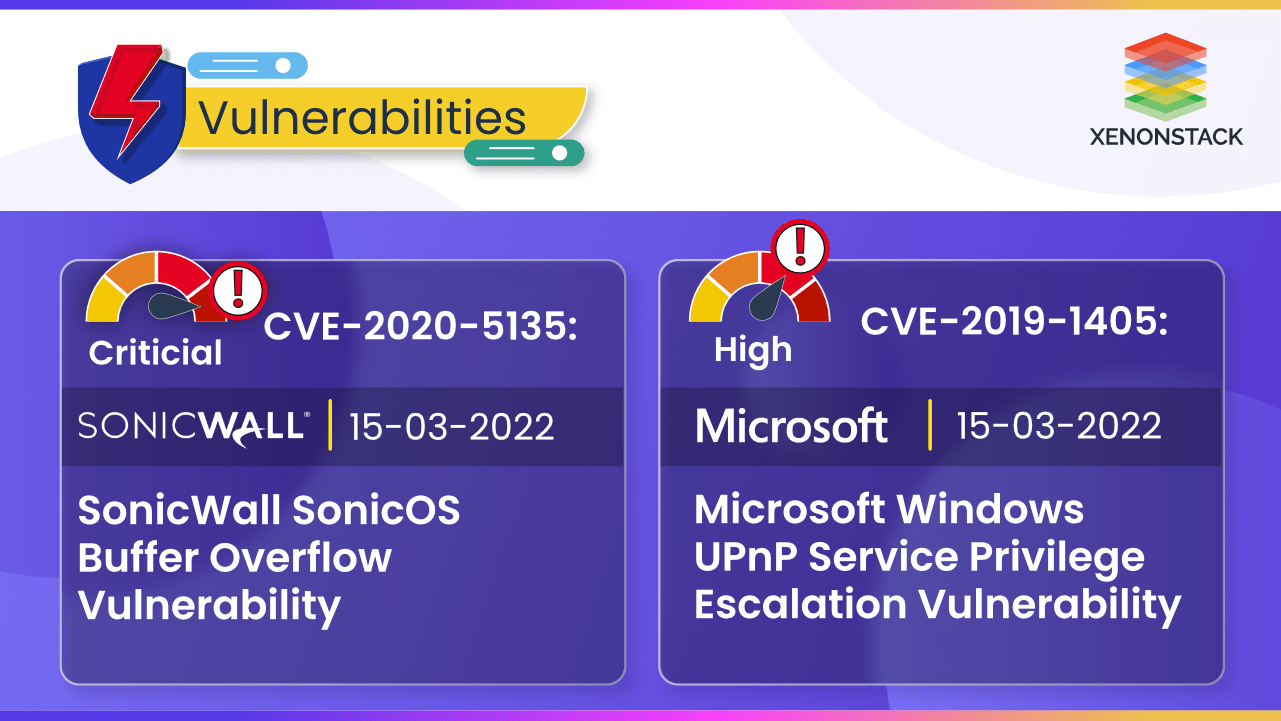
SonicWall's CVE-2020-5135 and Microsoft's CVE-2019-1405 vulnerabilities can cause disruption in the availability of resources
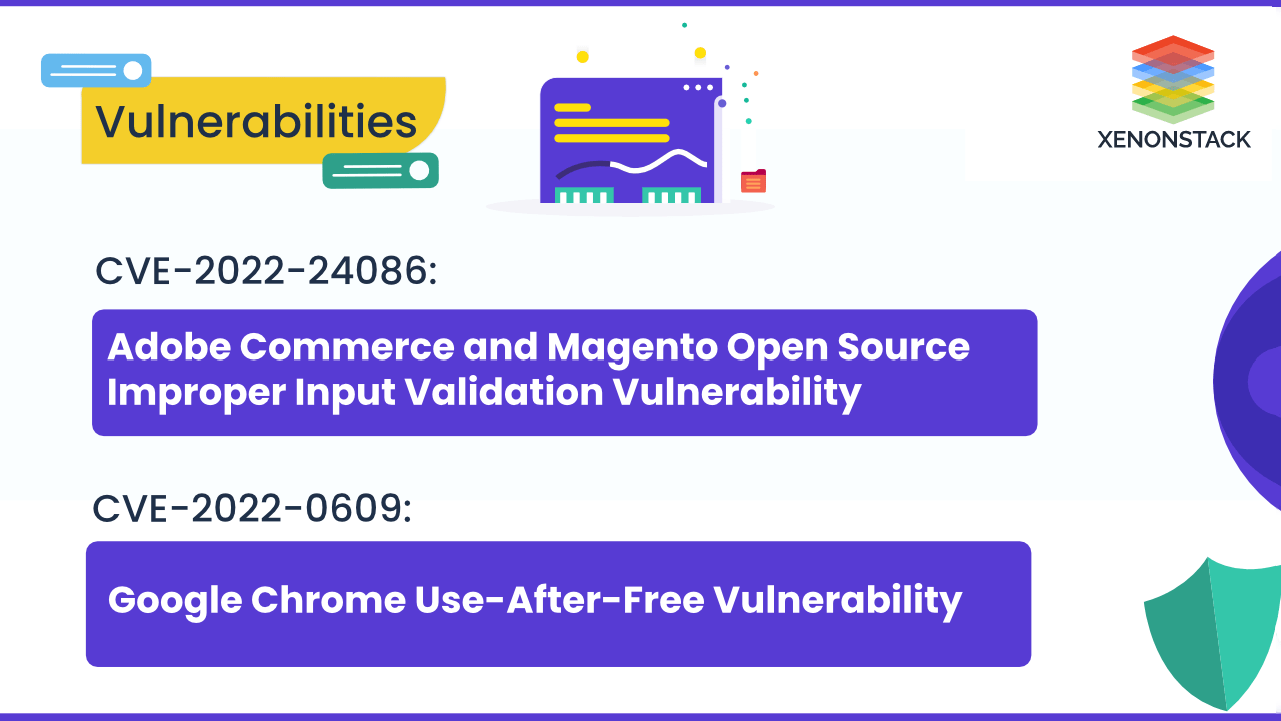
CVE-2022-24086 Vulnerability in Adobe Commerce and Magento Open Source and CVE-2022-0609 Vulnerability in Google Chrome allows arbitrary code ...

Zimbra Webmail Cross-Site Scripting (CVE-2022-24682) and Microsoft Office Remote Code Execution (CVE-2017-8570) vulnerabilities allow access to the ...
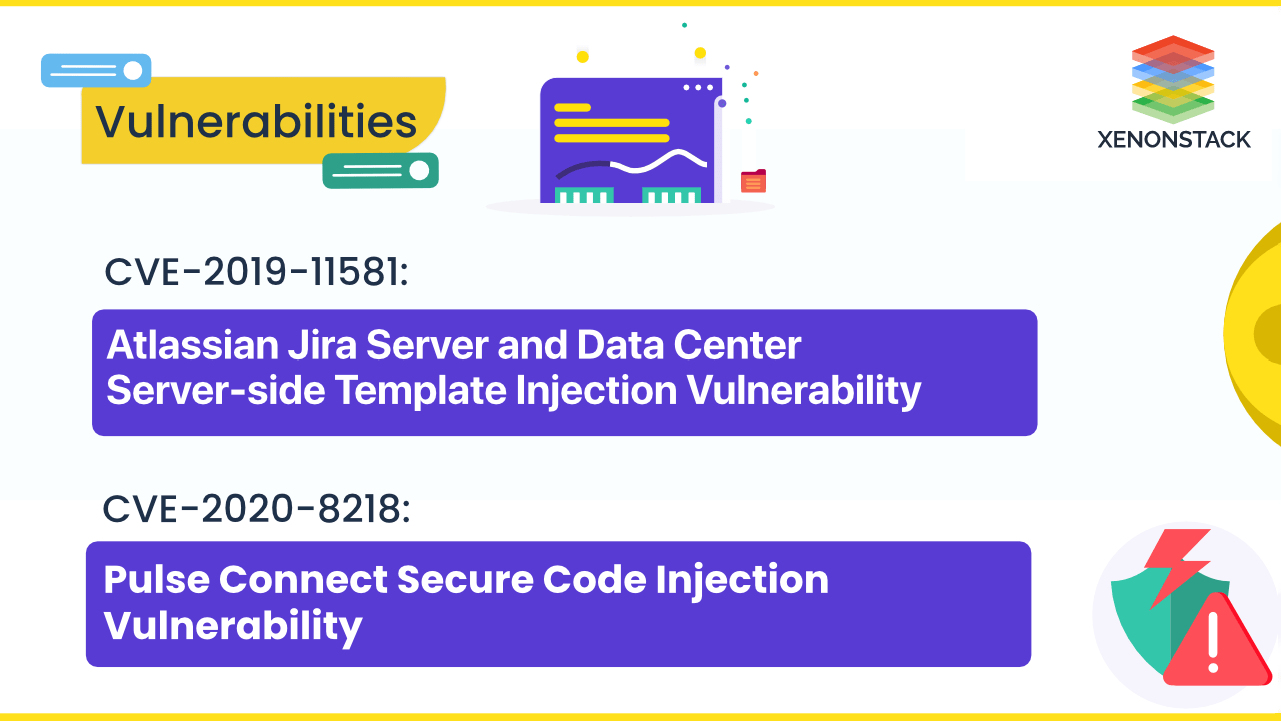
Atlassian Jira CVE-2019-11581 and Pulse Connect CVE-2020-8218 Injection Vulnerabilities allow attackers to execute arbitrary code

The VMware CVE-2021-21973 (SSRF) and NETGEAR CVE-2017-6077 (Remote Code Execution) Vulnerabilities have the potential to compromise your entire ...
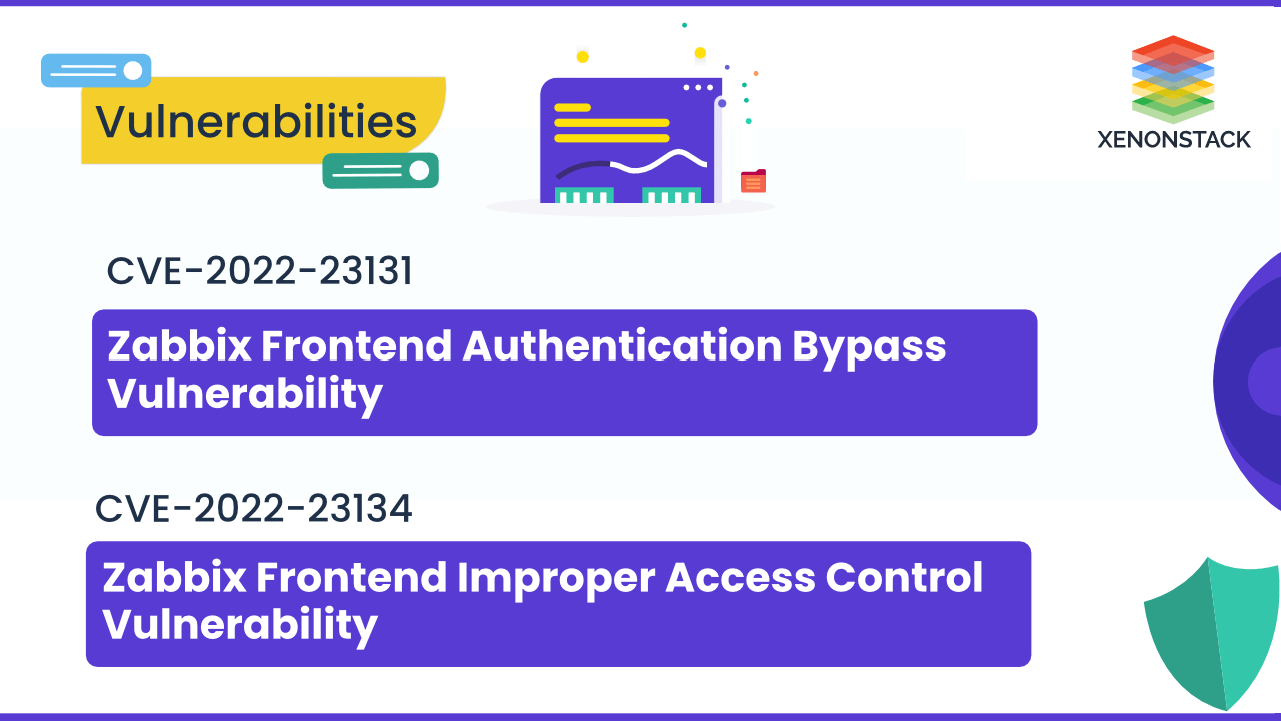
CVE-2022-23131 and CVE-2022-23134 Vulnerability in Zabbix Frontend could result in frontend settings alteration and Authentication instances takeover

Release Management Process Flow lifecycle, tools and Best Practices to manage the development, testing, deployment, and maintenance of software ...

Agentic Process Automation in Logistics & Supply Chain Management optimizes workflows, improving efficiency and decision-making

Learn effective strategies with The Ultimate Guide to Application Modernization Strategy for successfully upgrading your legacy systems.
Overview of benefits and Implementing DataOps as a Service in Enterprise to bring streamlined changes in data analytics throughout the life cycle
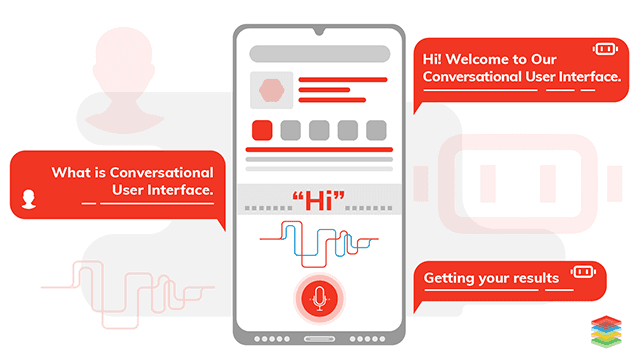
CUI tools, frameworks, and their applications are needed for the best customer experience strategy and design to interact with humans or AI bots.

Real-time intelligence is the process of delivering business intelligence about business operations as they happen in near-to-zero latency.

The transformative impact of ai and emergingtechnologies on the world of finance and banking
6 min | Dr. Jagreet Kaur

Comprehensive approach combines cost forecasting, resource optimization, and financial accountability
4 min | Dr. Jagreet Kaur

Unleashing data agents empowers real-time insights, driving smarter decisions and transforming business operations effectively
5 min | Dr. Jagreet Kaur
AI continuously monitors systems for risks before they escalate. It correlates signals across logs, metrics, and traces. This ensures faster detection, fewer incidents, and stronger reliability
AI converts camera feeds into instant situational awareness. It detects unusual motion and unsafe behavior in real time. Long hours of video become searchable and summarized instantly
Your data stack becomes intelligent and conversational. Agents surface insights, detect anomalies, and explain trends. Move from dashboards to autonomous, always-on analytics
Agents identify recurring failures and performance issues. They trigger workflows that resolve common problems automatically. Your infrastructure evolves into a self-healing environment
AI continuously checks controls and compliance posture. It detects misconfigurations and risks before they escalate. Evidence collection becomes automatic and audit-ready
Financial and procurement workflows become proactive and insight-driven. Agents monitor spend, vendors, and contracts in real time. Approvals and sourcing decisions become faster and smarter