What is CVE-2020-5135?
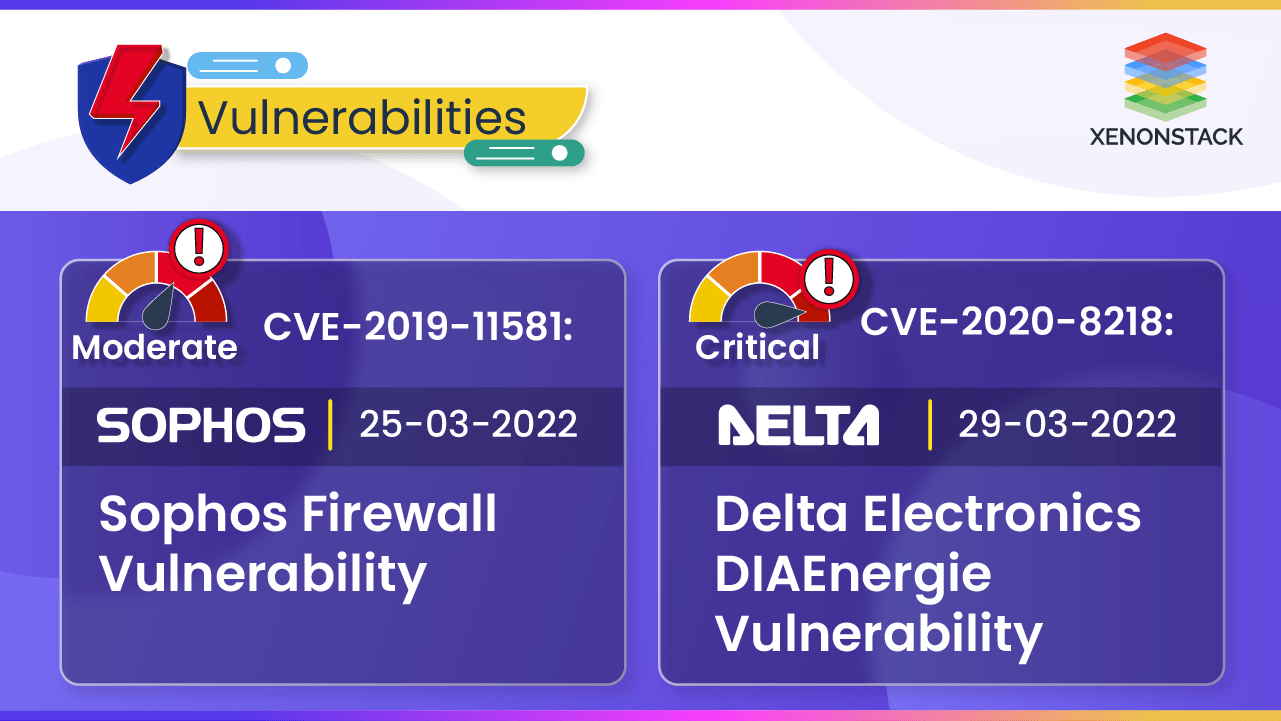
SonicWall SonicOS Buffer Overflow Vulnerability
SonicWall NSAs are next-generation firewall appliances that include a sandbox, an intrusion prevention system, SSL/TLS decryption and inspection, network-based malware protection, and VPN functionality.
This vulnerability exists before authentication and within a component (SSLVPN) that is frequently accessible to the public Internet.
CVE-2020-5135 is a stack-based buffer overflow flaw in SonicWall's Network Security Appliance's VPN Portal. A remote, unauthenticated attacker might exploit the flaw by submitting a specially crafted HTTP request with a custom protocol handler to a vulnerable device. According to the flaw's investigation, an unbounded string copy was being utilized to copy data from an HTTP request header directly into a response buffer without a proper length check.
At the very least, effective exploitation would cause the exploited device's resources to be depleted, resulting in a denial of service issue. According to the researchers, they were able to divert execution flow through stack corruption, implying that RCE is certainly doable. Hundreds of thousands of devices may be affected.
According to SonicWall, the following versions provide a workaround for this problem:
- SonicOS 6.5.1.12-1n
- SonicOS 6.0.5.3-94o
- SonicOS 6.5.4.7-83n
- SonicOS 6.5.4.v-21s-987
- Gen 7 7.0.0.0-2 and onwards
Impact of CVE-2020-5135
It is feasible to change some system files or information, but the attacker has no control over what can be changed, or the scope of what the attacker can affect is limited. There is a decrease in performance or a disruption in the availability of resources.
| CVE ID | CVE-2020-5135 |
| Vulnerability Name | SonicWall SonicOS Buffer Overflow Vulnerability |
| Vendor | SonicWall |
| Product | SonicOS |
| Description | By sending a malicious request to the firewall, a remote attacker can cause a Denial of Service (DoS) and potentially execute arbitrary code due to a buffer overflow vulnerability in SonicOS. |
| Date added to the catalog | 2022-03-15 |
| Severity (scale of 10) | 9.8 (Critical) |
| Remediation | As temporary mitigation, SSL VPN portals may be removed from the Internet before the patch is applied. |
What is CVE-2019-1405?
Microsoft Windows UPnP Service Privilege Escalation Vulnerability
When the Windows Universal Plug and Play (UPnP) service incorrectly authorizes COM object creation, an elevation of privilege vulnerability exists.
An attacker who successfully exploited this flaw may use elevated system access to launch arbitrary code. After that, an attacker might install applications, read, alter, remove data, or create new accounts with full user rights. An attacker would need to enter into an affected system and run a specially designed script or program to exploit this vulnerability.
The vulnerability is fixed by changing how the Windows UPnP service accesses COM objects.
It is extremely harmful to businesses because there are numerous ways to acquire access to any system within a company. In an organization with a domain controller, for example, every user with physical access to the domain can log in to any machine in the domain.
He can only access data on the machine that is exclusive to his user account.
Impact of CVE-2019-1405
Computers running Microsoft Windows 10 1803 are vulnerable to these flaws.
The integrity of the system has been completely compromised. The system's protection has been completely lost, putting the entire system at risk. The impacted resource has been completely shut down. The attacker has the ability to make the resource utterly unusable.
| CVE ID | CVE-2019-1405 |
| Vulnerability Name | Microsoft Windows UPnP Service Privilege Escalation Vulnerability |
| Vendor | Microsoft |
| Product | Windows Universal Plug and Play (UPnP) |
| Description | When the Windows UPnP service incorrectly authorizes COM object creation, an elevation of privilege vulnerability arises. |
| Date added to the catalog | 2022-03-15 |
| Severity (scale of 10) | 7.8 ( High) |
| Remediation | Only allow trusted individuals local access. Use limited contexts and shells whenever possible. Make sure only trustworthy users have local, interactive access to the computers in question. |
Conclusion
SonicOS authorizes a remote attacker to force Denial of Service (DoS) and potentially execute arbitrary code by sending a malicious request to the firewall and UPnP vulnerability improperly authorizes COM object creation, aka "Windows UPnP Service Elevation of Privilege Vulnerability".