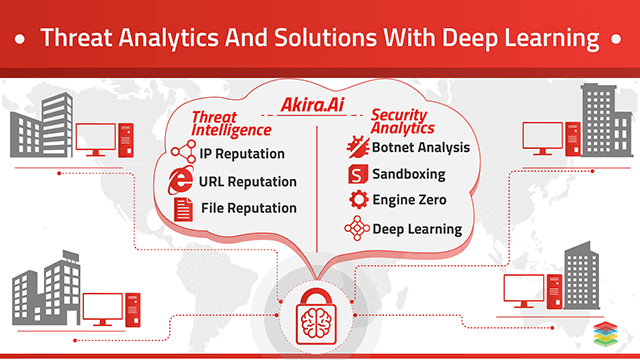
What are the challenges of Cyber Security Analytics?
In today’s era, a wide variety of technologies are available in the market. Every individual wants to use that not only in a professional way but also in their personal life. But as technologies increase, the risk for organizations or individuals also increases. Because intrusive hacking is becoming both more sophisticated and widespread, the organization’s security team has to collect and use the historical data on accounts, machines, and equipment that may have been attacked to predict, identify and prevent the potential new threats this all can be possible with cyber security analytics.What are the Solutions for Cyber Security Analytics?
With Xenonstack Support, security analytics is divided into four sectors; users will predict attacks and prevent them before something serious.Digital Security
- In digital security analytics, by using a dataset containing the historical data of the protocol used, type of attacks, source IP address, source port number, destination IP address, and destination port number, the entity can build, deploy, and refresh the models to predict incoming threats in real-time.
- Our prediction model allows analysts to monitor intrusion vectors and take action as soon as possible and protect the system from serious causes.
Data Security
- In Digital Security, One can protect the database, computer system, and websites from attack by doing analysis. For which CIA traits were violated, assets targeted penetration data and other information sources.
- Through this, an entity can find threats or attacks at an earlier stage and take action as early as possible.
Network Security
- In Cyber Security by Network Security analytics, one can build accurate and predictive models on real-time data to better understand the customer to get the information about their attacks, Vulnerabilities, events logs, and authentication user can bring clarity to the network connectivity.
- As a result, we have given the demo of the dashboards for user reference. You will be confident after getting the results for events logs, attack prediction results, etc. By seeing the dashboards, you will get information about how our machine-learning models work.
Communication Security
- In Communication Security analytics, one can build accurate and predictive models on real-time data. To better understand the customer to get the information about their communication of message delivery, encryption for TLS and Non-TLS between the networks.
- And here, the user will see the prediction on messages delivered through emails that are authenticated.
- As a result, we have given the demo of the dashboards for reference. You will be confident after getting the results for the encryption of messages, authentication, and spam filters using our machine-learning model. Users can easily get all the information about communication network security by applying our models.
Why Xenonstack?
Click on the button and request us to give you a demo of our machine learning model for cyber security analytics. Here you will get insights related to attacks, network security, communication, digital security, and data security. Our model will provide you with the accurate prediction of attacks and message delivery for our security analytics model with narrative addition.
Dashboards
Below are the security analytics dashboards for every four sectors for users to predict attacks and prevent them before something serious.
Digital Security
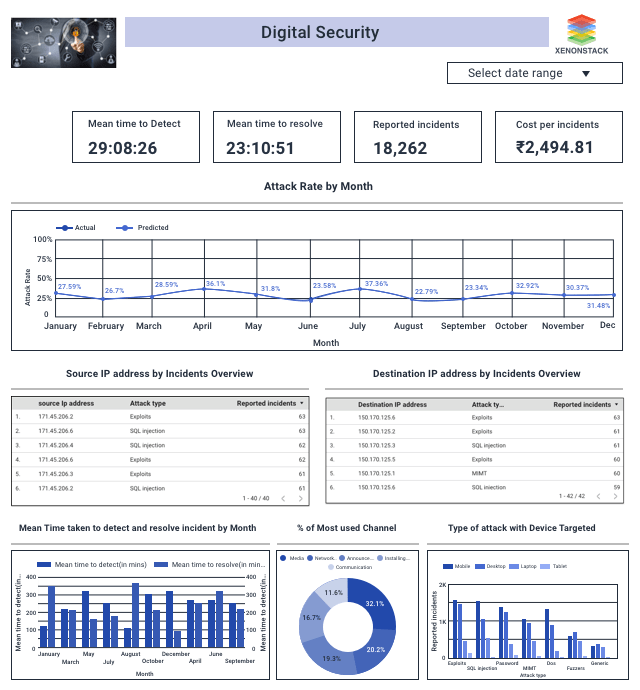
Description of Digital Security Dashboard
- We analyze server logs from the above dashboard to find the source IP address and protocol used to reach the destination IP address.
- Here we are calculating the average mean time taken to detect and resolve the issue each month.
- Several attacks with sub-categories representing this attack happened along with a count of their subcategory.
- The line chart predicts attacks in the coming year.
Data Security
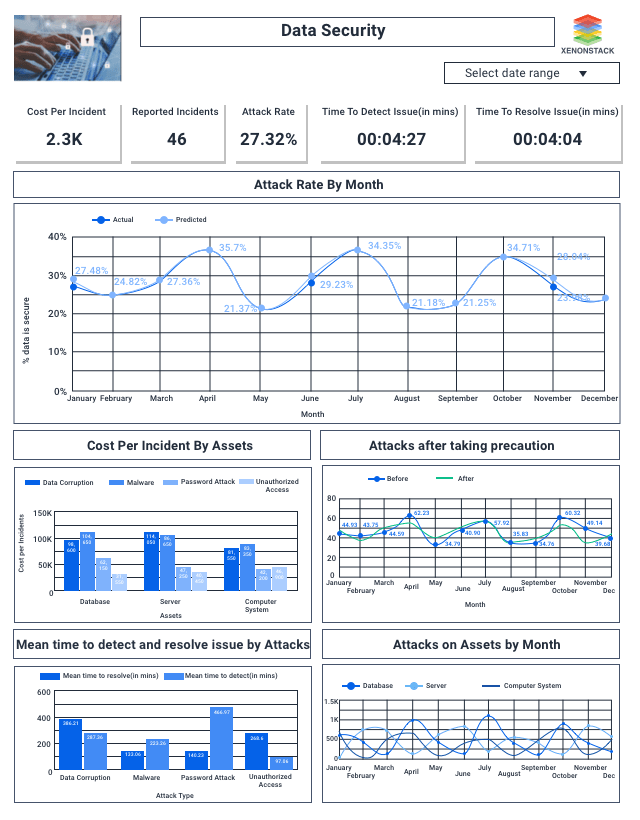
Description of Data Security Dashboard
- We analyze which asset the attacker tries to attack and through which attack they attacked from the above dashboard.
- The bar chart shows that when an attacker is on the database, he/she tries through malware.
- Here we are calculating the time taken to find an attack and solve that issue.
- An upper-right bar chart predicts attacks or threats in the coming year.
Network Security
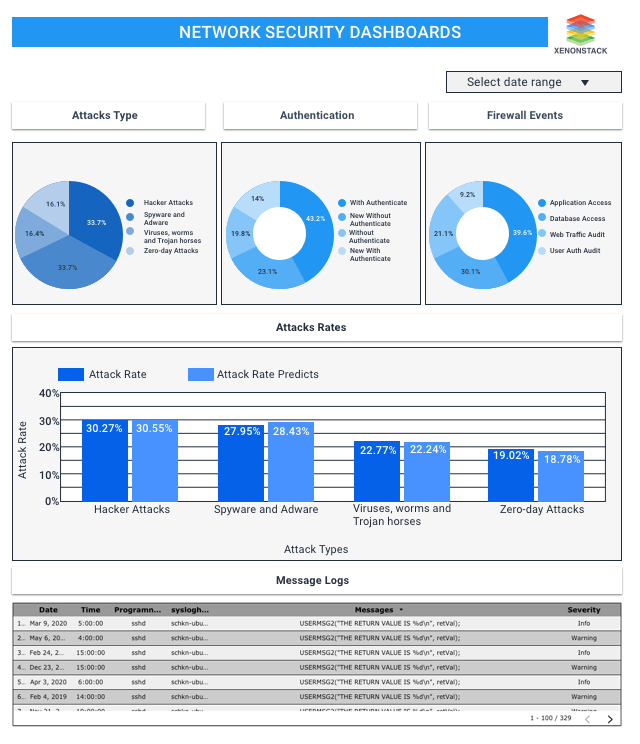
Description of Network Security Dashboard
- Here are dashboard shows the firewall events, authentication, attack type, and prediction to see the vulnerabilities like critical, high, medium, and low.
- So here, users will get information about attacks through which they can see the max attacks from which hacker attacks and several events logs in the morning around eight, and our prediction model will show the attacks predicted from different types of attacks. Here, users will also get the results on authentication and firewalls.
Communication Security
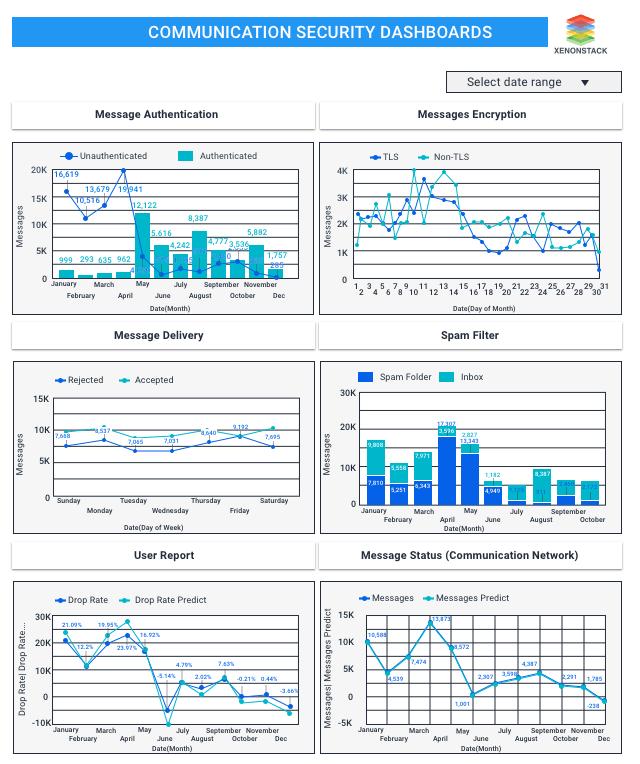
Description of Communication Security
- Here are dashboard will show you the communication status of security through messages, spam filters, and encryption of messages when they are delivered.
- Here, users can see the messages delivered with user confirmation on rejected and accepted weekly. We will also get the details about encrypting messages daily.
- Our prediction models will give the results on messages predicted every month.
.webp?width=1921&height=622&name=usecase-banner%20(1).webp)