A Brief Introduction to Compliance as a Code
Compliance as a Code is that the idea of taking paper-based administrative compliance for the cloud, and moving it into the code delivery pipeline, by putting it away as arrangement within the code base, sitting accessible the asset/administration/part that it'll check for compliance once the Code becomes animated and is shipped into the cloud. It helps to characterize your compliance prerequisites using a human and machine-coherent language. Configurations would then be ready to be automatically deployed, tested, monitored and reported. This automation comes as Code and incorporated into the code archives utilized by Developers and Engineers.
The Evolution of Compliance as Code
An enterprise has adopted DevOps in the few years to enhance its software development and delivery process; process compliance is neglected to incorporate faster delivery processes during the development.
Over the past few years, organizations worldwide are now concerned about security and compliance to the requirement of several compliance standards such as GDPR, ISO 27001, HIPAA, PCI DSS, etc., which currently holds business importance. Compliance with the standard has led to introducing security and compliance in the early phases of the software development lifecycle, impacting the whole process. Security is not the same as compliance.
If you think compliance is expensive, try non-compliance
— Former U.S. Deputy Attorney General Paul McNulty
Compliance requirements are very complex to correlate and understand. Auditing the entire ecosystem for compliance is very time-consuming and costly. Also, it requires much human effort. But, humans tend to make mistakes, and sometimes even the security team is not aware of the exact requirements stated by the compliance standards. This situation has led to the concept of looking at 'compliance to standards' as Compliance-as-Code, which is now an integral component of DevSecOps and validates DevOps infrastructure compliance. It helps to insert and enforce compliance requirements into the development pipeline to ensure that every release meets the security baseline standards.
What is Compliance as Code?
Compliance-as-Code means using programmatic methods (code) for automating the implementation, validation, remediation, monitoring, and reporting of the required compliance standards that an organization needs to be compliant with across the entire organization's ecosystem.
The most prominent advantage of using Compliance-as-Code is that it can be used and integrated across the whole compliance lifecycle process. It can be used in the initial design and implementation phase to validate different controls' implementation. It may also be used for performing continuous monitoring and remediating the potential issues. Usage of compliance-as-code enables monitoring of the compliance status and provides a report on the CI/CD pipeline if integrated into your CI/CD. Incorporating the compliance-as-code also allows you to monitor real-time changes, validate the differences concerning the desired compliance standards, and report the compliance status.
Compliance is measured against security requirements, such as regulatory compliance and internal governance, benchmarks, and best practices. When adopting compliance-as-code, you need to determine the security benchmarks and best practices that you need to follow and regulatory & internal governance requirements to be compliant with. Once you have determined all the requirements and appropriate controls, you need to translate those requirements and specified controls into specific rules using code. Finally, you need to integrate or execute these codes to validate a specified resource/service and determine whether that specified resource/service is compliant with the determined requirements and controls.
How does Compliance as a Code Work?
People usually write compliance rules of non-technical background in-short simple language which could be easily understood but for making it work the rules need to be converted from the non-technical format to Code, Compliance as a Code for that developer needs to change the requirements and rules into machine-readable Code. The main motive of this conversion is to dissociate the specification, implementation, and enforcement of compliance rules into Code. 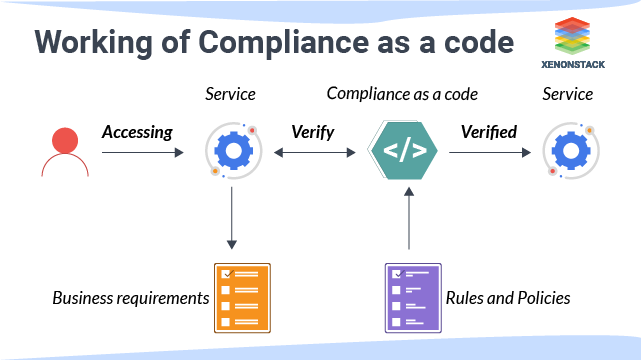 The job of checking and evaluating Code and any new change is done by the help of Compliance as a Code tools which trigger the appropriate actions when any change happens. Tools keep a check on the code and application change in a way that nothing new could affect the rules stated in compliance. One of the popular and efficient tools for compliance as a Code in the market is OPA(Open Policy Agent).
The job of checking and evaluating Code and any new change is done by the help of Compliance as a Code tools which trigger the appropriate actions when any change happens. Tools keep a check on the code and application change in a way that nothing new could affect the rules stated in compliance. One of the popular and efficient tools for compliance as a Code in the market is OPA(Open Policy Agent).
Why Compliance as Code is needed?
Compliance as Code helps you understand what compliance checks are going through at each stage of your entire software delivery process. Applying Code from the very beginning of the development process helps the risk and development teams to do their jobs faster so that the delay does not happen. It brings teams up to define policies and rules. This allows teams to create standards and templates that can be shared across the organization, allowing DevOps to scale. The main benefit of complying with the Code is that it allows you to write tests rather than configuration. Writing tests allow you to be much more granular than the editorial writing code.
Here are 4 reasons on why compliance as code is needed for businesses
- Compliance as Code and CI/CD pipeline
- Compliance as Code and Audit Trail
- The Compliance Knowledge Gap
- Agility with Compliance as Code
Compliance as Code and CI/CD pipeline
Let's assume that compliance-as-code is built into the CI/CD pipeline; the developers will come to know the compliance status on every commit and make changes accordingly. In this way, the final version will be 100% compliant. Compliance-as-Code is required over manual enforcement of compliance requirements and the controls as it provides a way for continuous monitoring and reporting of compliance status.
Compliance-as-Code helps provide greater visibility on the different rules validated at each step of the software development life cycle. Incorporating compliance-as-code such as shift-left security from the beginning of the software development lifecycle helps the security team determine the risks. Also, the development team to make changes at the early stages leading to on-time delivery, reducing the cycle time, and both the teams can perform their jobs faster.
CI/CD mechanisms are applied to test server configuration, server image building, environment provisioning and the mixture of environments. Click to explore about, How to Implement Infrastructure as Code in CI/CD Pipeline?
Compliance as Code and Audit Trail
The audit trail is one of the most critical aspects of compliance. An audit trail must answer the following questions: what was the change? Who made the change, who requested the change, and why? Was the change tested? Who reviewed the change? was the change tested before being made? Who tested the change? When was the test performed? when was the change made?. Following the principle of compliance-as-code provides an audit trail for every change that is made.
Validating and auditing compliance using Compliance-as-Code helps achieve a very high precision as it depends on programmatic methods. When compliance depends on manual processes, the results may be too error-prone as humans tend to make errors; scalability is also more effortless even in cloud environments. If the environment is scaled up, the defined programmatic methods can also be scaled to match the environment and validate compliance status. Thus, repeatability of the entire process can be achieved very easily, reducing the total level of effort required to deploy and maintain compliant workloads.
The Compliance Knowledge Gap
Adopting Compliance-as-Code integrated the compliance requirements and controls into different business processes as a mandatory practice. It helps to decrease the compliance knowledge gap. It also helps to prioritize the compliance tasks. For instance, let's say that your automated reports give a list of 20 non-compliant applications. So, you can easily prioritize them based on the criticality of your business needs. It also streamlines the routine reporting process and helps to achieve transparency over the entire compliance process that the management can easily track.
Agility with Compliance as Code
When using compliance-as-code, the compliance rules are written as code, and all the checks are automated. So, you can quickly run your compliance checks again and again after making minor changes to validate the compliance status. It also supports automated evidence gathering defined programmatically, simplifying the audit preparation and assessment process. One of the significant advantages of having compliance rules written as code is that the rules can easily be tested, versioned, and categorized into bundles, known as compliance bundles. Compliance violations can also be grouped, visualized, and be reported to a centralized dashboard to increase the compliance status visibility.
What are the Benefits of Compliance as Code for Business?
Compliance as code provides benefits across your organization.
- Complete Visibility across the organization
- Scale compliance effortlessly
- Avoid Surprises
- Easier Management of Compliance Requirements
Complete Visibility across the organization
Adopting Compliance-as-Code helps an organization to achieve visibility across its ecosystem. The stakeholders can quickly know what's going on across the organization regarding compliance status at any given point in time. The organization can easily maintain an audit trail across everything across the development lifecycle and determine a proper risk acceptance score. It also helps the organization evaluate any process's deviations from the minimum compliance requirements.
Scale compliance effortlessly
Compliance-as-Code helps the organization efficiently and adequately scale compliance requirements across the organization. Once the compliance requirements have been converted into codes and scripts and organized into compliance bundles, the entire ecosystem can be easily validated and audited to ensure compliance. Saling compliance requirements also become more manageable as these compliance bundles can easily be integrated, and automated checks can be performed. It enhances the efficiency of both the security team and the development team as these automated checks allow the development team to check the compliance status at any given point of time without bothering or taking support from the security team who can focus on other security challenges. The security team can release a new compliance bundle when compliance requirements change.
Avoid Surprises
Compliance-as-code helps enterprises to articulate the compliance status with zero surprises. When compliance-as-code is integrated into different processes, the organization can rest assured the outcome will be 100% compliant. Any non-compliant scenario can be easily traced and will not be allowed to move forward in the production process until all the compliance rules are followed are successfully validated.
In case of sudden events such as emergency production changes and zero-day vulnerabilities, it becomes easier to maintain compliance by identifying the required machines/object of change and fixing/changing things faster as security standards are integrated into the business processes.
Easier Management of Compliance Requirements
Compliance-as-Code solves the biggest problem of understanding the compliance requirements. Compliance requirement documents are typically very elaborate and complicated to understand. Compliance-as-Code solves this problem by converting those compliance requirements into automated scripts and codes that anyone can quickly validate without understanding the entire compliance requirement documents. It reduces the cost involved in managing, auditing, and ensuring compliance throughout the entire organizational process. It helps gather evidence and generate audit reports easily and quickly. It also helps to ensure the scalability and reliability of compliance status.
How to implement compliance as code in businesses?
Different tools need to be used in different phases of the software development lifecycle to implement Compliance-as-Code. In the planning phase, organizations can use the SecurityRAT open-source tool provided by OWASP. It lets the team create security requirements as code integrated into every project as an auditable artifact.
In the build phase, organizations can use TruffleHog, Gitty Leaks, or Git-Secrets to check for secrets in source code. In this phase, tools such as OWASP Dependency-Check, or retireJS can check for vulnerabilities in known components and vulnerable dependencies. Organizations can use InSpec by Chef and Open Policy Agent (OPA) tools in the testing phase. For CI/CD, another tool called Conftest, based on OPA, can validate various requirements. Conftest helps you write tests against structured configuration data. Using Conftest, you can write tests for your Kubernetes configuration, Tekton pipeline definitions, Terraform code, Serverless configs, or any other config files.
In the case of Kubernetes, Gatekeeper tool is built on top of OPA to validate and audit kubernetes resources both pre and post-deployment. In the deployment phase, organizations prefer CIS benchmarks to harden the industry best practices' systems/services. IT automation frameworks such as IT Chef, Puppet, or Ansible can be used for this purpose
Open Policy Agent(OPA)
An open policy agent is an open-source, standard policy engine that integrates policy enforcement across a stack. OPA provides a high-level language that allows you to specify policy as code and easy APIs to load policy decisions from your software. You can use OPA to enforce policies on microservices, Kubernetes pipelines, CI / CD pipelines, API gates, and more. It uses a declarative language called Rego for querying the data.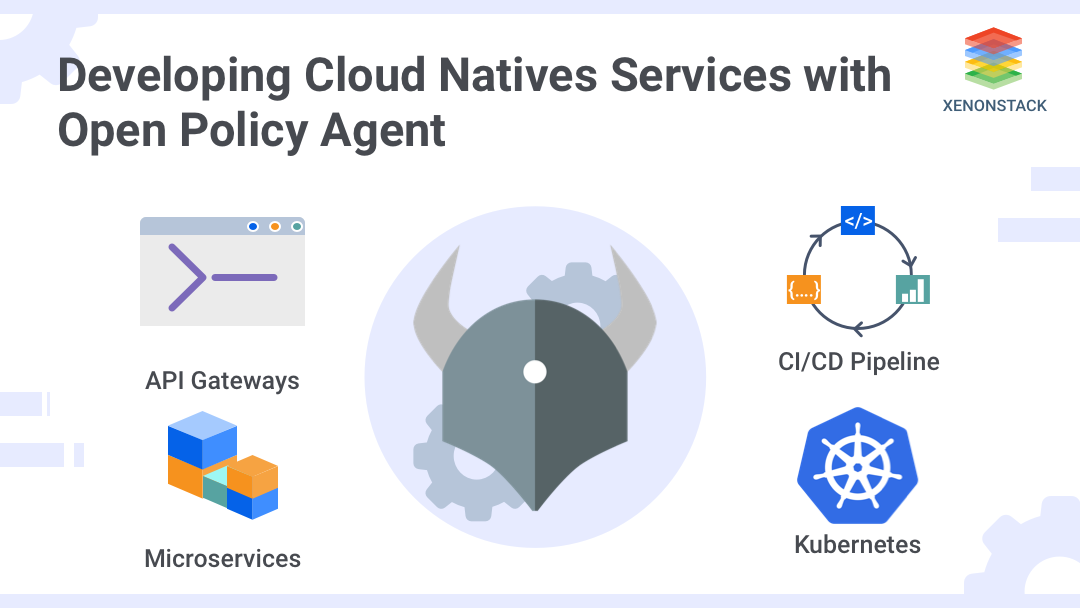
OWASP Security RAT
Open Web Application Security Project improves the security of software through its community-led open-source software projects that produce freely-available articles, methodologies, documentation, tools, and technologies in the field of web application security. OWASP Security Requirement Tool deals with security requirement management during development using automation approaches. The focus of Security RAT is put on automation rather than the requirements.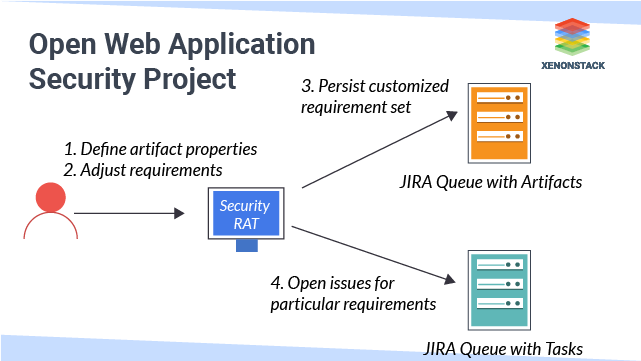
What are the best practices of Compliance as Code?
Some of the essential best practices that need to be followed when implementing Compliance-as-Code are:
- Prioritize shift-left security and integrate Compliance-as-Code from the beginning of the process chain.
- Perform thorough testing of the developed security rule to ensure that they don't violate requirements.
- Consider all the end cases while defining the rules.
- Deploy and test the test environment's policies before deploying them into the production environment.
- Regularly check for the required modification in policies with changes in compliance standards.
- Security assessment of application and infrastructure should not be avoided even if Compliance-as-Code is implemented.
- Automated security reports should be thoroughly reviewed.
- Always remember all compliance requirements are not always necessary to enforce.
Conclusion
Compliance as a Code brings management, compliance, internal audit, as well as development and implementation. The policies and rules for compliance and control need to be defined by all the stakeholders working in partnership. Managers need to understand how operational risks and other risks will be managed and managed through the pipeline. Ability to incorporate their requirements as a code so that their organizations can access those artefacts on their teams at scale and ultimately allow compliance to be another Quality Assurance element in the software you submit. It is good to monitor continuously the compliance of the systems and provide evidence of such monitoring to external or internal auditors.
Implementing Compliance-as-Code from the very beginning of the development lifecycle ensures the timely delivery of a project that tends to be compliant. It allows the security team to build templates and scripts, which can be shared across the organization enabling greater scalability. Compliance is an essential aspect of business and has become a requirement for organizations' growth and development
What's Next?
- Know how Infrastructure as code implemented in organization
- Learn more about AI in IT Infrastructure Management
- Access the GDPR Compliance Checklist
.webp?width=1921&height=622&name=usecase-banner%20(1).webp)


