In today's fast-evolving digital landscape, security can no longer be an afterthought. As cyber threats become more sophisticated and damaging, organizations recognise the need to integrate security throughout the development lifecycle. Enter DevSecOps—a transformative approach that embeds security within DevOps practices, ensuring applications are secure by design rather than as an afterthought.
What is DevSecOps?
DevSecOps, which stands for development, security, and operations, is a software development practice that integrates security into the development process. It is an approach to providing security to applications and infrastructure based on the DevOps methodology, which ensures the application is less vulnerable and ready for users' use. All things are automated, and security checks start from the beginning of the application's pipelines. Selecting the right tools for Continuous Integration security achieves security goals, but the selection of tools is not enough; security teams also need the right tools to meet the required security.

Fig 1: DevSecOps
DevOps vs DevSecOps: Key Differences
While DevOps aims to streamline collaboration between development and IT operations for rapid delivery, it traditionally overlooked security until the final stages. DevSecOps, however, injects security controls early and continuously throughout the pipeline. This proactive approach mitigates risks before they escalate, ensuring that the code is secure from the first commit.
|
Aspect |
DevOps |
DevSecOps |
|
Primary Focus |
Speed and collaboration between development and operations |
Security integrated into development and operations |
|
Security Integration |
Applied mostly at the final stages of the SDLC |
Applied from the beginning and throughout the pipeline |
|
Risk Management |
Reactive—security issues often addressed after deployment |
Proactive—risks are identified and mitigated early |
|
Responsibility |
Security is often the concern of a separate team |
Shared responsibility across development, security, and operations teams |
|
Tools and Automation |
Focus on CI/CD tools and automation for delivery |
Includes CI/CD tools plus automated security tools integrated into the pipeline |
|
Speed vs. Security |
Prioritizes speed of delivery |
Balances speed with continuous security assurance |
Why is DevSecOps Important?
-
Security from the Start: DevSecOps ensures that security is embedded from the beginning of the development lifecycle, not added as an afterthought. This approach helps identify and fix vulnerabilities during design and development rather than in production.
-
Faster, Safer Releases: By integrating automated security tools into CI/CD pipelines, teams can release software faster without sacrificing security. It eliminates the traditional trade-off between speed and safety, enabling secure, continuous delivery.
-
Reduced Risk of Data Breaches: Continuous scanning, monitoring, and threat detection reduce the chances of security breaches. Since security is a continuous process, vulnerabilities are caught before being exploited in production environments.
-
Compliance Made Easy: DevSecOps simplifies compliance with industry regulations and standards by automating policy enforcement and audit trails. Security controls are built into the pipeline, ensuring consistent compliance across all deployments.
-
Cost Savings: Fixing vulnerabilities during development is significantly cheaper than addressing them post-release. DevSecOps reduces the long-term costs of incidents, investigations, fines, and reputational damage.
-
Supports Innovation at Scale: With security automated and integrated, teams can innovate rapidly without fear of introducing critical flaws. This model supports agile development and scalability without compromising on protection.
Key Components of DevSecOps
A successful DevSecOps process is built on four core pillars that tightly integrate development, operations, and security across the software lifecycle
Continuous Integration (CI): In CI, developers frequently commit code to a shared repository, often multiple times a day. Automated builds and tests run with each commit, helping teams identify and fix integration issues or bugs early—before they escalate into larger problems later in the pipeline.
Continuous Delivery (CD): CD extends CI by automating the movement of code from build to staging environments. Here, additional tests—like UI validation, API checks, and load testing—are run to ensure that the application functions correctly and is production-ready. This process ensures reliable and consistent delivery of software that meets user expectations.
Continuous Security: Security is embedded throughout the entire software development lifecycle, not just at the end. From early threat modeling to automated static and dynamic security testing, DevSecOps emphasizes continuous assessment. Developers are empowered to identify and fix vulnerabilities in their own environments, promoting a "secure-by-design" approach.
Communication and Collaboration: DevSecOps thrives on tight collaboration between development, security, and operations teams. Open communication helps resolve code conflicts quickly, align on security goals, and maintain shared accountability for delivering secure, high-quality software. Culture is just as important as tools in making DevSecOps successful.
Why Organizations Need DevSecOps
With rising cyber threats, regulatory pressures, and fast-paced software cycles, DevSecOps is no longer optional. Here's why it’s become a necessity, not a choice:
Reduced Security Vulnerabilities in Production
One of the most significant risks in traditional development is discovering vulnerabilities after software is released. These post-deployment flaws often go unnoticed until exploited, leading to data breaches, outages, or regulatory violations.
DevSecOps shift security left—ensuring threats are identified and fixed early, drastically reducing the number and severity of issues in production environments.
Lower Costs of Remediation
Fixing security flaws late in the development cycle or after release is exponentially more expensive—often up to 30 times more costly than fixing them during coding or testing.
By integrating automated security tools and practices throughout development, DevSecOps helps catch and resolve issues early, saving significant time, resources, and budget.
Faster Time-to-Market Without Compromising Security
Speed is essential in modern software delivery, but it often comes at the expense of thorough security checks. DevSecOps eliminates this trade-off by embedding automated, continuous security checks within CI/CD pipelines.
This enables teams to release updates and features faster, with built-in security that doesn’t slow down innovation.
Improved Compliance Management
Organizations in regulated industries must comply with frameworks like GDPR, HIPAA, PCI DSS, and SOC 2.
DevSecOps tools help enforce these policies automatically through code scanning, audit trails, and infrastructure checks—making compliance more straightforward to achieve and maintain without manual overhead.
Enhanced Collaboration Between Teams
DevSecOps breaks down silos between development, security, and operations teams. Instead of treating security as an isolated task, it becomes a shared responsibility.
This cultural shift fosters collaboration, encourages transparency, and empowers all stakeholders to contribute to building secure and resilient software from day one.
DevSecOps Pipeline Architecture
Understanding the CI/CD Pipeline Integration
DevSecOps integrates security directly into CI/CD pipelines, embedding protection mechanisms within each stage of the software development lifecycle. Instead of security being a final checklist before production, it's a continuous and automated process. This allows teams to detect and resolve security issues earlier when they're easier and cheaper to fix.
-
With every code commit, security tools automatically scan for vulnerabilities, insecure code patterns, or secrets left in the code.
-
During builds and deployments, automated policies ensure that only safe, validated artefacts move forward.
-
This design ensures speed and security go hand-in-hand, giving developers real-time feedback without blocking the delivery cycle.
A DevSecOps-enabled CI/CD pipeline is proactive rather than reactive, reducing the risk of last-minute delays caused by unresolved security flaws.
DevSecOps Lifecycle Phases with Integrated Security Checkpoints
The DevSecOps lifecycle enhances the traditional DevOps pipeline by embedding security controls, processes, and accountability into every phase of software development. Instead of treating security as a final gate, DevSecOps distributes it across the lifecycle, enabling proactive risk mitigation and faster remediation. Below is a breakdown of each phase, along with the security checkpoints embedded at each stage:

Fig 2: DevSecOps Pipeline
1. Plan
Security begins at the planning stage, where teams conduct threat modelling and risk assessments and define security requirements for upcoming features. This ensures the system is designed with a secure architecture from the start.
Security Checkpoints
-
Threat modelling sessions to identify potential vulnerabilities early
-
Definition of security acceptance criteria
-
Risk and compliance assessments integrated into planning
2. Code
In this phase, developers are empowered with secure coding practices and tools to catch vulnerabilities while writing code. Using Static Application Security Testing (SAST), code is scanned for flaws like buffer overflows or injection attacks before it's committed.
Security Checkpoints
-
SAST tools integrated into IDEs and CI systems
-
Secure coding guidelines enforced through linters and policies
-
Peer code reviews with a focus on security risks
3. Build
During the build process, tools perform Software Composition Analysis (SCA) to detect known vulnerabilities in third-party dependencies. Additionally, container image scanning ensures Docker images are free from misconfigurations and malicious packages.
Security Checkpoints
-
Automated SCA to flag outdated or insecure libraries
-
Container scanning tools to detect vulnerabilities or hardcoded secrets
-
Build policy enforcement to block unsafe artefacts
4. Test
Security testing goes beyond functionality checks and includes Dynamic Application Security Testing (DAST) to simulate real-world attacks. API security testing ensures endpoints are not susceptible to data breaches or abuse.
Security Checkpoints:
-
DAST to uncover runtime issues like XSS or broken authentication
-
API testing for access control, injection flaws, and rate limiting
-
Integration of fuzz testing for unexpected inputs and edge cases
5. Release
Before pushing code to production, the release phase includes final vulnerability assessments, compliance validations, and penetration testing to confirm the application meets security and regulatory standards.
Security Checkpoints:
-
Penetration tests to mimic real-world attackers
-
Automated scans for residual vulnerabilities
-
Compliance verification with standards like OWASP, GDPR, HIPAA, etc.
6. Deploy
Deployment pipelines leverage Infrastructure-as-Code (IaC) scanning tools to verify that security policies are enforced consistently across environments. This ensures production setups are hardened and compliant.
Security Checkpoints
-
IaC policy checks using tools like Open Policy Agent or Checkov
-
Validation of secure cloud configurations and access controls
-
Detection of misconfigured permissions, open ports, or insecure storage
7. Operate
Once the application is live, security doesn’t stop. Continuous monitoring, Runtime Application Self-Protection (RASP), and log analysis help detect threats, respond quickly, and ensure the system behaves securely under real-world conditions.
Security Checkpoints:
-
Runtime monitoring and anomaly detection using SIEM or XDR tools
-
Behavior analysis and RASP for real-time attack protection
-
Log collection and audit trails to support incident response
By embedding tailored security checks into each DevSecOps lifecycle phase, organizations can quickly detect, isolate, and resolve issues without slowing down development. This “fail-fast, fix-fast” approach reduces risk, increases agility, and ensures a secure and reliable software delivery pipeline.
Integrating Security into the CI/CD Pipeline
To ensure security at every step, DevSecOps integrates multiple security mechanisms into Continuous Integration (CI) and Continuous Deployment (CD) pipelines. Let’s break down how security is applied in CI/CD:
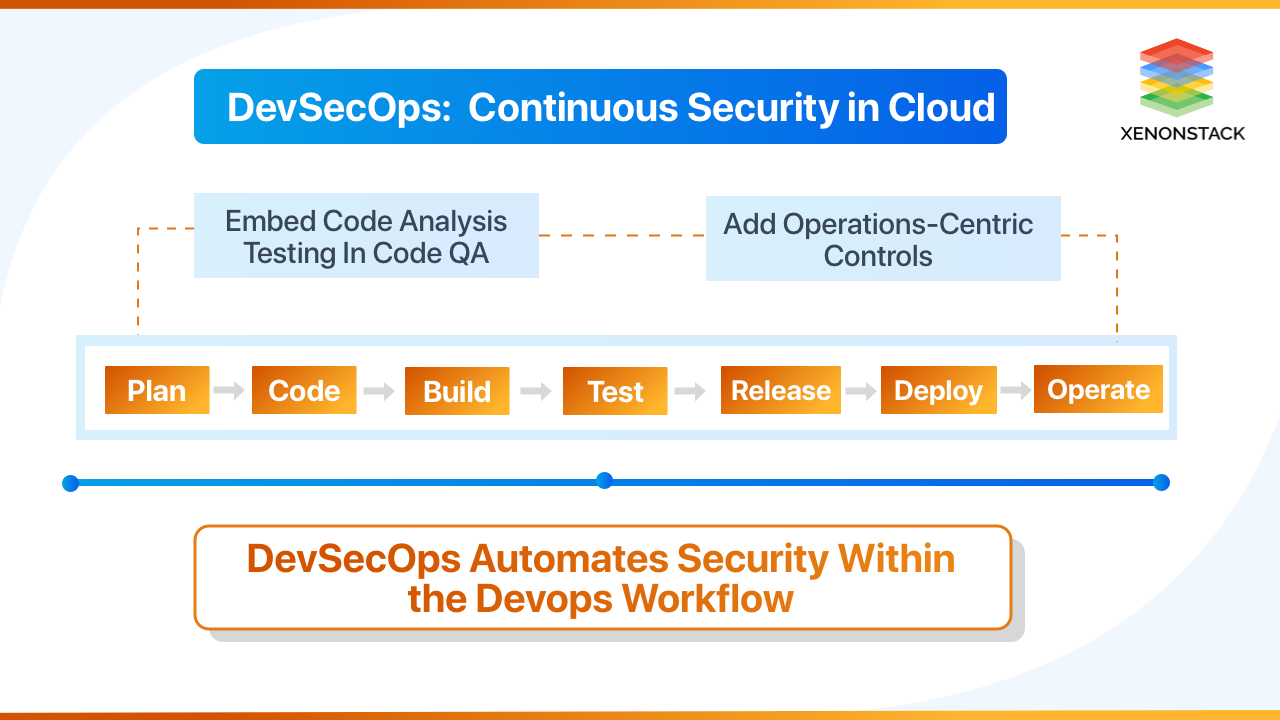
Fig 3: DevSecOps: Continuous Security
-
Static Application Security Testing (SAST): SAST tools analyze code before execution to identify vulnerabilities early. They scan source code, bytecode, or binaries for security flaws. Popular tools include SonarQube, Checkmarx, Fortify, and GitHub CodeQL.
-
Dynamic Application Security Testing (DAST): DAST tests applications in a running state, simulating real-world attacks to detect security flaws like insecure authentication and SQL injection. Common tools are Burp Suite, OWASP ZAP, Acunetix, and AppScan.
-
Container and Infrastructure as Code (IaC) Security: Container security scanning ensures Docker and Kubernetes environments are free of vulnerabilities. IaC security verifies Terraform, AWS CloudFormation, and Ansible scripts against misconfigurations. Secret management tools prevent hardcoded sensitive data. Tools include Trivy, Clair, Aqua Security, Sysdig Secure, Checkov, Terrascan, Cloud Custodian, HashiCorp Vault, AWS Secrets Manager, and Doppler.
DevSecOps Tools and Technologies
A well-structured DevSecOps pipeline relies on a combination of security, monitoring, testing, and automation tools to identify vulnerabilities, enforce compliance, and ensure the application remains secure throughout the software development lifecycle (SDLC). Below are some essential DevSecOps tools, along with their functionalities:

Fig 4: DevSecOps Tools
Automated Testing Tools
-
[Code]AI: An intelligent application that automatically identifies and fixes security vulnerabilities in source code, supporting multiple programming languages and integrating with platforms like GitHub and GitLab.
-
Parasoft Tool Suite: Provides comprehensive automated software testing, including functional, security, and performance testing.
Application Security Testing Tools
-
Checkmarx CxSAST: A static analysis platform that identifies security vulnerabilities in proprietary and open-source code across 25+ languages.
-
Veracode: A cloud-based testing tool offering static, dynamic, and mobile application security analysis.
-
BDD-Security: A security testing framework leveraging Behavior-Driven Development concepts.
-
Chef InSpec: An open-source framework for testing and auditing application infrastructure.
-
Fortify: A comprehensive static code analysis tool with integrated build capabilities.
Log Management Tools
-
Splunk: A powerful platform for searching, monitoring, and analyzing machine-generated data in real-time.
-
SumoLogic: Similar to Splunk, it collects and analyzes log data to generate visualizations, reports, and alerts.
-
Scalyr: A cloud-based solution for log management, visualization, and alerting.
-
Nagios: Provides monitoring, alerting, and logging capabilities.
Monitoring Tools
-
ExtraHop: Offers visibility into complex infrastructure communications to identify congestion points.
-
Datadog: An application performance management tool that monitors all aspects of software infrastructure.
-
SignalFx: Processes and displays monitoring data in customizable dashboards.
-
Tripwire: A configuration control solution that monitors configuration compliance.
Alerting Tools
-
VictorOps: Provides incident visibility and facilitates cross-team communications.
-
PagerDuty: A SaaS-based incident response platform with AI-driven automated responses.
-
OpsGenie: An incident management platform for alerts and on-call management.
-
Alerta: Accepts alerts from various sources and associates metadata with warnings.
-
ElastAlert: A framework for alerting on patterns in Elasticsearch data.
Dashboard Tools
-
Grafana: An open-source analytics and visualization web application that works with various time-series databases.
-
Kibana: Part of the ELK Stack, providing visualization capabilities for data indexed on Elasticsearch.
Threat Modeling Tools
-
IriusRisk: An open threat model platform for creating and managing security risks throughout the development lifecycle.
-
ThreatModeler: An automated threat modeling solution for identifying, predicting, and defining threats.
-
OWASP Threat Dragon: An open-source tool for creating threat model diagrams and recording threats.
DevSecOps techniques
-
Static application security testing (SAST): Rigorously test applications for functionality
-
Continuous penetration testing: Integrate security into the development pipeline to identify and mitigate vulnerabilities in real-time
-
Access controls: Manage who can access systems and data to reduce unauthorized access
-
Security as code: Develop a culture where security workflows can be automated
DevSecOps Implementation Strategy
Building an Effective DevSecOps Culture
Culture is a critical component of successful DevSecOps implementation. Organizations must foster a culture where:
- Security is everyone's responsibility: Shifting from the traditional model where security is solely the security team's job to a model where developers, operations, and security teams all share responsibility. This cultural shift requires leadership buy-in and clear communication about expectations and responsibilities.
- Teams collaborate across traditional boundaries: Breaking down silos between development, operations, and security teams by implementing shared goals, joint planning sessions, and cross-functional teams. This collaboration enables better communication and more effective security implementations that don't hinder development speed.
- Learning from failures is encouraged: Creating an environment where security incidents are treated as learning opportunities rather than blame exercises. Post-incident reviews should focus on process improvements and preventive measures, not finding individuals to blame.
- Continuous improvement is valued: Establishing processes for regular review and improvement of security practices. This includes gathering feedback from all stakeholders, measuring the effectiveness of security controls, and iteratively enhancing security measures based on lessons learned.
- Security knowledge is shared openly: Promoting transparency around security concerns, vulnerabilities, and incidents. Organizations should create channels for sharing security knowledge, such as internal blogs, lunch-and-learns, and communities of practice, to elevate everyone's security awareness.
DevSecOps in Microservices and Cloud-Native Applications
As organizations shift towards microservices and cloud-native architectures, security must be embedded across API communication, identity management, and infrastructure security.
1. API Security in Microservices
-
APIs expose microservices to both internal and external consumers, making them prime targets for cyberattacks.
-
Implementing API security best practices:
-
OAuth 2.0 and OpenID Connect for authentication.
-
Rate limiting and API gateways (Kong, Apigee, AWS API Gateway) to prevent DDoS attacks.
-
Automated API security testing (42Crunch, APIsec) to detect vulnerabilities in API contracts.
-
2. Identity and Access Management (IAM)
-
Implement Role-Based Access Control (RBAC) and Principle of Least Privilege (PoLP) to restrict unauthorized access.
-
Use Multi-Factor Authentication (MFA) for additional security layers.
-
Tools like Okta, Auth0, and AWS IAM help enforce secure access policies.
3. Container and Orchestration Security
-
Kubernetes Security Best Practices:
-
Use Kubernetes network policies to restrict traffic between services.
-
Enable Pod Security Policies (PSP) or Open Policy Agent (OPA) to enforce security compliance.
-
Secure Kubernetes clusters with Kube-bench, Kube-hunter, and Falco.
-
-
Service Mesh Security (Istio, Linkerd):
-
Encrypt microservices communication with mTLS (Mutual TLS).
-
Implement fine-grained security policies at the service level.
-
DevSecOps Governance Framework
A strong governance framework establishes security policies, coding standards, third-party security requirements, risk thresholds, and accountability to align security with business goals.
-
Compliance Monitoring: Automated compliance checks and continuous monitoring ensure adherence to security standards. Proper documentation, regular reporting, and remediation workflows help maintain compliance.
-
Risk Management: Risk assessments, regular reviews, prioritization, and mitigation strategies help manage threats. Risk acceptance processes ensure informed decision-making.
-
Vulnerability Management: Continuous scanning, prioritization, and remediation of vulnerabilities prevent security gaps. SLAs, tracking, and verification processes ensure effective resolution.
-
Security Training and Awareness: Regular secure coding training, security awareness programs, role-based training, and threat intelligence sharing build a strong security culture. Security champions promote best practices across teams.
DevSecOps Best Pratices
Adopting DevSecOps is more than just integrating security tools into your CI/CD pipeline—it’s about creating a culture of shared responsibility, continuous improvement, and automation-driven security. Here are some best practices to help organizations implement DevSecOps effectively.
Shift the Culture Toward Security-First Thinking: Encourage collaboration across teams to integrate security into development workflows. Foster a culture of continuous learning and adaptation to security challenges.
What are the challenges of implementing DevSecOps?
Companies might encounter the following challenges when introducing DevSecOps to their software teams.
-
Resistance to the cultural shift: Software and security teams have been following conventional software-building practices for years. Companies might find it hard for their IT teams to adopt the DevSecOps mindset quickly. Software teams focus on building, testing, and deploying applications.
Meanwhile, security teams focus on keeping the application safe. Therefore, top leadership needs to get both teams on the same page about the importance of software security practices and timely delivery.
-
Complex tools integration: Software teams use different types of tools to build applications and test their security. Integrating tools from different vendors into the continuous delivery process is a challenge. Traditional security scanners might not support modern development practices.
Future Trends in DevSecOps
The future of DevSecOps is evolving rapidly with new technologies and methodologies enhancing security integration in the software development lifecycle.
-
Zero-Trust Security: Eliminates implicit trust by requiring continuous authentication, least privilege access, and strict verification for all users and devices. This prevents unauthorized access and minimizes insider threats.
-
Shift-Right Security: Extends security beyond development by focusing on runtime security testing, real-time threat detection, and canary deployments in production. This helps identify vulnerabilities that traditional testing might miss.
-
Security Chaos Engineering: Intentionally injects security failures into production environments to test resilience and response strategies. This approach strengthens defenses by preparing systems for real-world attack scenarios.
-
Security Observability: Provides real-time monitoring and deep visibility into security logs, attack patterns, and system behavior. This helps teams detect and respond to threats faster with actionable insights.
-
Continuous Compliance: Integrates automated compliance checks into CI/CD pipelines to enforce security policies and regulatory standards (e.g., GDPR, ISO 27001). This ensures ongoing compliance without manual intervention.
-
AI and Machine Learning in DevSecOps: AI-driven tools enhance security through automated vulnerability detection, predictive analytics, and intelligent threat response. This reduces human workload and speeds up security incident resolution.
Next Steps with DevSecOps
Talk to our experts about implementing a robust DevSecOps pipeline, leveraging cutting-edge tools and governance frameworks to enhance security, automate compliance, and accelerate software delivery
.webp?width=1921&height=622&name=usecase-banner%20(1).webp)




