
Introduction to DevOps
DevOps was born to help developers and operations teams to work better. IT has been accepted as a standard practice. But with the rise in zero-day exploits and the need to quickly restore services and make them secure by design, it only makes sense to factor security into DevOps. Thus, Security Testing in DevOps is it not only important but an essential. If security is not taken care of delay in the software delivery can cause affects in brand and customer loyalty.
What is Security Testing?
It is a type of software testing that ensures that any application or system is free from threats, vulnerabilities, and risks.- It is about finding all possible weaknesses of the system, which might result in a loss of data or information of an organization.
- Security Testing helps in detecting all possible security risks in the system and assist developers in fixing these problems through coding.
A process in which, Modern software engineering Culture and Practices to develop software where the development and operation teams work hand in hand as one unit. Click to explore about, What is DevOps and it's Processes
Why do we need Security Testing in DevOps?
- Security testing is essential to safe Data records lost and stolen by other industries.
- To avoid loss of customers' trust.
- For securing web applications to unauthorized hackers.
- Security testing help in improving the current system and also helps in ensuring that the system will work for a longer time.
- To avoid website downtime, time loss and reduce the cost of recovering from the damage.
- Security tests help in finding out loopholes that can cause loss of valuable information.
What are the Principles of Security Testing?
The basic principles of Security testing in DevOps are listed below:
- Confidentiality
- Integrity
- Availability
Let us discuss them one by one.
Confidentiality
This is equivalent to security, and it has a set of rules which limit access to any information. It protects against disclosure of information to an unauthorized person. It ensures that only the delegate person gets and access the data.Integrity
Integrity is like consistency and accuracy of data over its entire life cycle, and allows transferring accurate and desired data without any modification from senders to intended receivers. It ensures that unauthorized people cannot modify data.Availability
In availability need to maintain all data, hardware and, software, performing hardware and software repairs immediately when required. It is essential to ensure that the information concerned is readily accessible to the authorized viewer at all times.The approach of taking the action of testing the software and moving it to the left in the delivery pipeline. Click to explore about, Shift Left Testing Benefits and Approach
What are the best Security Testing Tools?
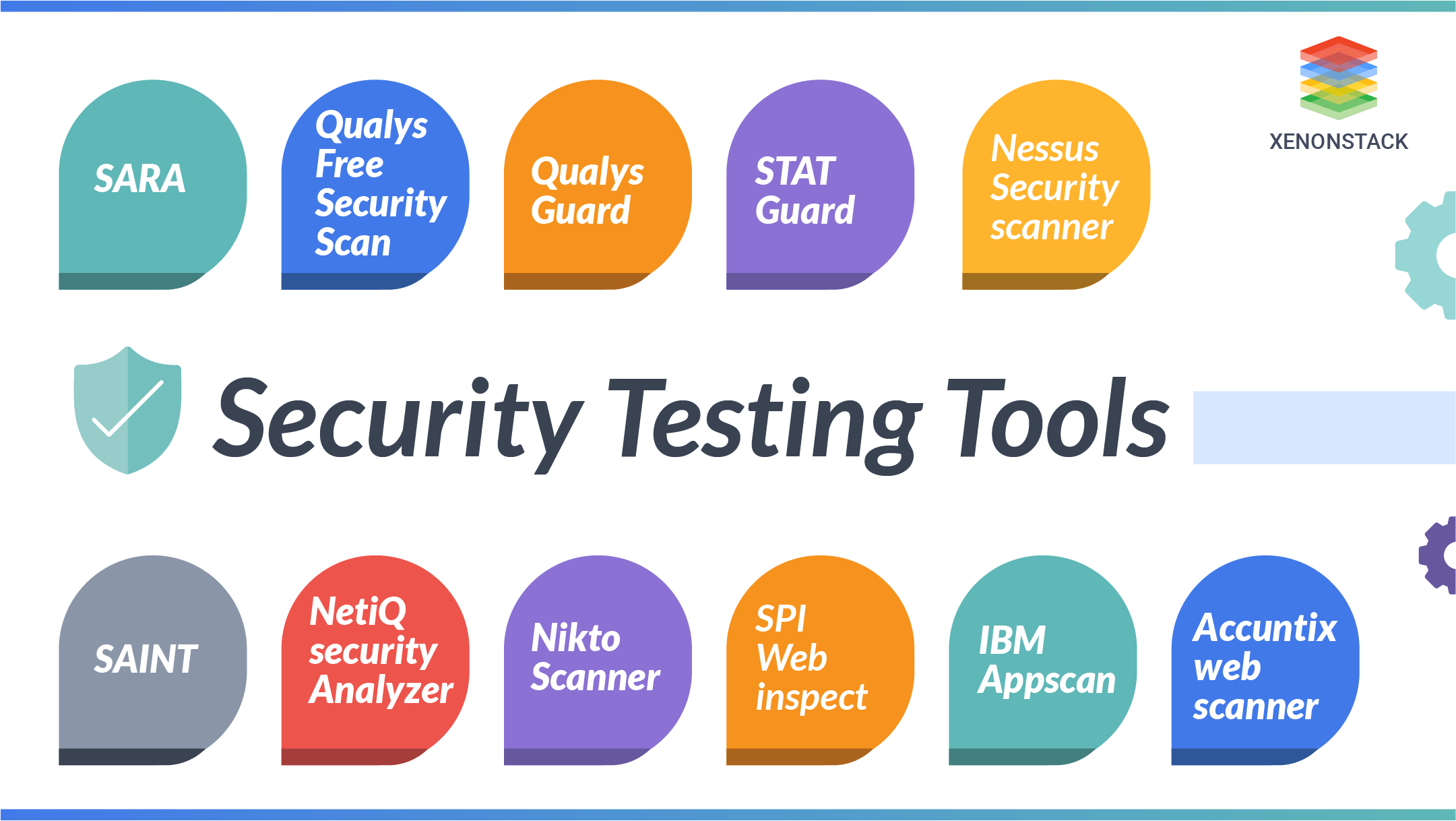 The best security testing tools are mentioned below:
The best security testing tools are mentioned below:
- SARA
- Qualys Free Security Scan
- Qualys Cloud Platform
- STAT Guard
- Nessus Security Scanner
- SAINT
- NetiQ Security Analyzer
- Nikto Scanner
- SPI WebInspect
- IBM Appscan
- Acunetix Web Scanner
What are the various categories of Security Testing in DevOps?
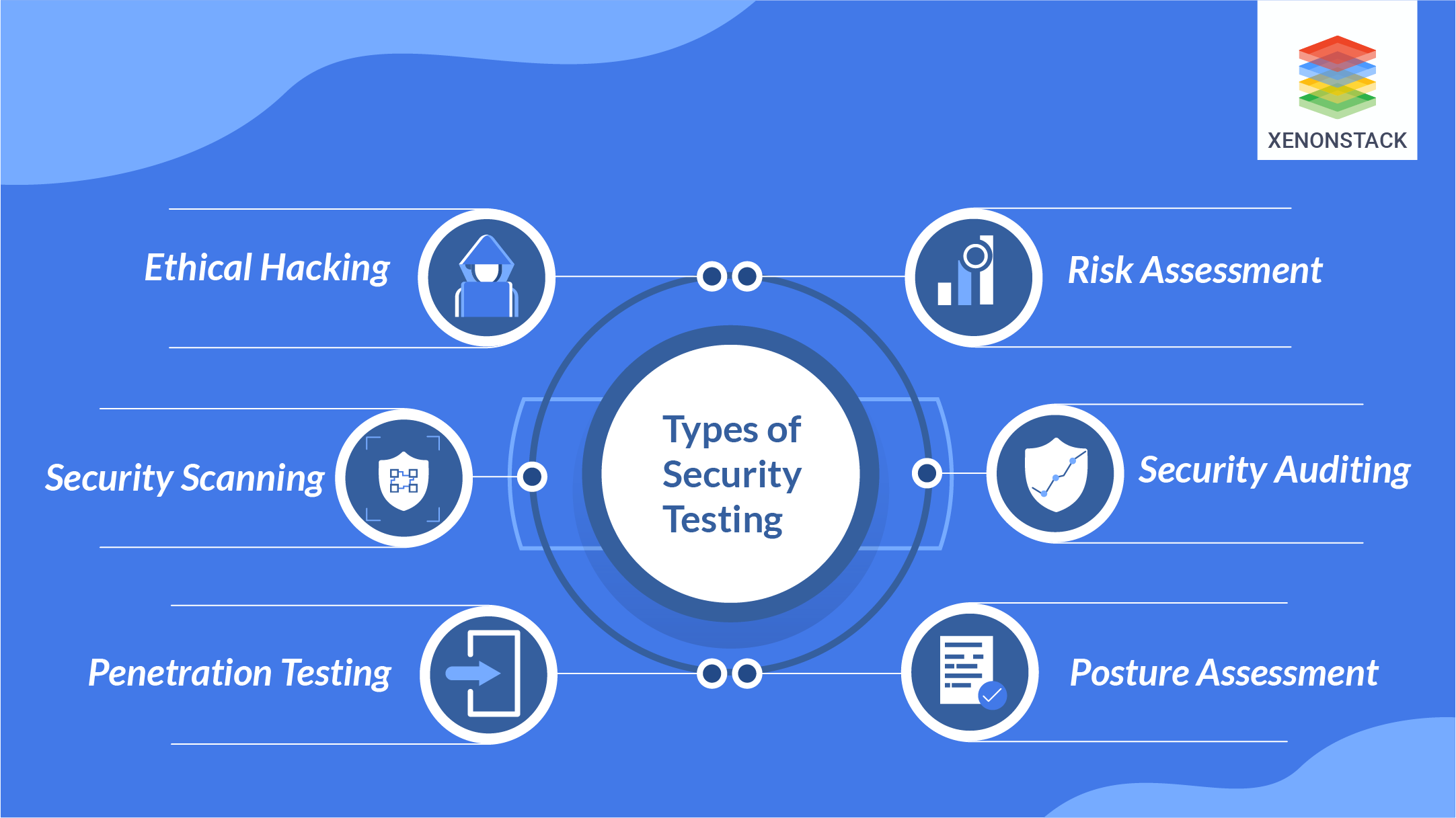
Vulnerability Scanning
In this old testing system under test is scan to find out the vulnerable signatures here we verify the access control with the operating system and technology adoptivePenetration Testing
An attack from hackers is a similar attack under the system under examination. Penetration Testing can be used to find a web application security policy ever. It targets the assets of the company that is visible on the internet like a company website, email access.Ethical Hacking
Here system under test is an attack from within to exposes all the security issues in the application software. Ethical Hacking is a part of a mature application security program to ensure continuous security thorough out the organization and its application.Risk Assessment
The assessment of risk involves the security of the system under test is done. And then the likelihood is classified as high, medium and low bases of certain factors.Security Scanning
They are studied in detail, analyzed and fixed the problems. It scans all the systems under test and finds out the weaknesses of the network.Security Review
A security review process used to identify security-related issues. This the review process for security.Test automation is the utilization of specialized software to control the execution of tests and the comparison of actual outcomes with predicted results. Click to explore about, Test Automation in DevOps
What are the areas of Security Testing implementations?
- Network security: Looking for vulnerabilities in the network infrastructure.
- System software security: Testing weaknesses in the various software (operating system, database system, etc.)
- Client-side application security: This will check that the client-side browser cannot be manipulated.
- Server-side application security: This involves making sure that the server code is free from all possible intrusions.
What are the advanced Techniques of Security Testing?
The below highlighted are the advanced Techniques of Security Testing in DevOps:
- SQL injection.
- Cross-site scripting (XSS).
- Session expiry.
- URL manipulation.
- Cross-site request for forgery(CSRF)
SQL injection
It fetches the data through the database and display on the web application to users. In this case, web application generates a SQL query and this SQL query hast to send to the database where it is executed, and the database sends to the relevant result to the web application. By using SQL injection, we manipulate the SQL query and make it a malicious question. SQL injection is a code injection technique used to execute malicious statements.Cross-site scripting (XSS)
Cross-site scripting refers to a client-side code injection attack wherein an attacker can execute a malicious script (also commonly referred to as a malicious payload) into a legitimate website or web application. It is mainly divided into three types:-- Reflected XSS
- Stored XSS
- DOM XSS
Cross-site Request for forgery
Malicious website requests a legitimate website on which the user is authenticated. The Request is triggered by a malicious website on behalf of the user. The browser automatically sends cookies and session ids.Example of Security Testing
- A Strong password policy is taken care of.
- Password is stored in encrypted form
- Login/Logout functionality
- For financial and banking application, the browser back button should not work.
- In banking application credit card/Debit card. Passwords etc. should flow in an encrypted format.

Security and DevOps with Xenonstack
Xenonstack enables automated application security solutions and services to secure the software that drives enterprises. With a unified platform for assessing and improving application security from inception through production by implementing DevSecOps and threat intelligence, Xenonstack enables organizations to innovate with trust as they build, buy and assemble applications.
Conclusion
Security breaches are among the most significant threats faced by various organizations today. There have been numerous cases of data breaches, which makes the need for proper Continuous Security in place. Better security enhances a software product’s use in the market and builds trust with consumers.
- Discover more about SRE Approach to Achieve DevOps
- Explore here the Role of Agile in DevOps


